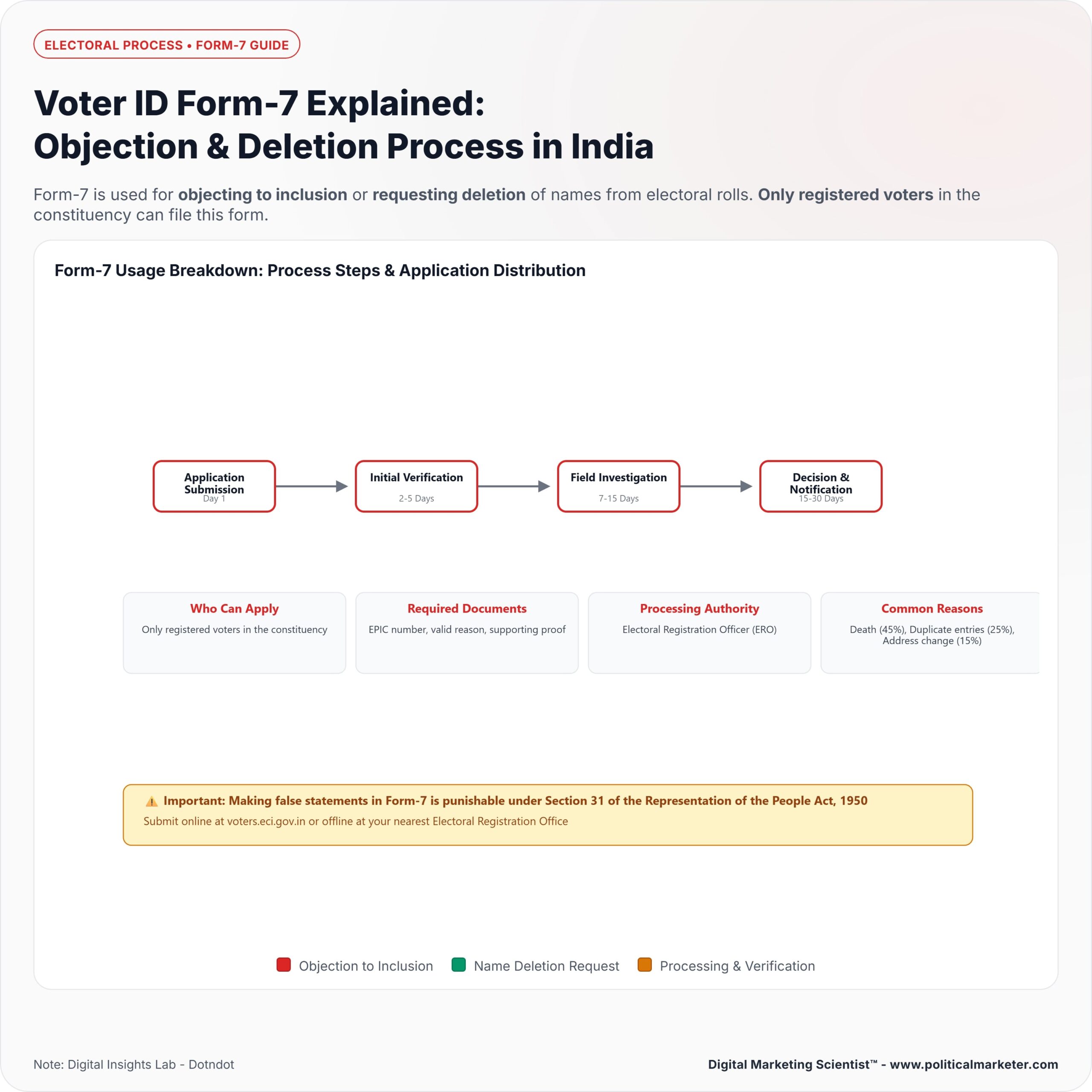
Voter ID Form-7 is a statutory form under the Representation of the People Act, 1950, used to apply for the deletion of a voter’s name from the electoral roll.
The purpose of this form is legitimate: it allows citizens, political parties, or officials to request the removal of entries when a voter has died, shifted residence, or is otherwise no longer eligible in a given constituency.
It is an important tool for keeping the voter lists accurate and up to date. However, because it can be filed online through the NVSP portal, VHA app, or GARUDA system, it also creates potential for misuse if malicious actors submit bulk deletion requests without proper verification.
What Does Voter ID Form-7 Do in India?
Voter ID Form-7 is used to request the deletion of a voter’s name from the electoral roll in India. It is meant for legitimate cases such as when a person has died, moved out of the constituency, or is otherwise ineligible to vote there.
The form helps maintain accurate voter lists, but since it allows removal of names, it requires strict verification by Election Registration Officers to prevent misuse and wrongful deletions.
Purpose of Form-7
Form-7 exists to keep electoral rolls updated. Citizens, family members, or officials can use it to request deletion of a voter’s name when the person has:
-
Passed away.
-
Moved permanently to another constituency.
-
Lost eligibility due to legal or statutory reasons.
Who Can File It
Any voter, close relative, or designated election official can submit Form-7. Political parties may also file requests in bulk during voter roll revisions, but these must undergo strict verification to prevent misuse.
How It Is Submitted
Form-7 can be filed both offline and online:
-
Offline: Through the Electoral Registration Officer (ERO) at the local election office.
-
Online: Via the National Voter Service Portal (NVSP), Voter Helpline App (VHA), or GARUDA platform.
Verification by Election Authorities
Once submitted, the ERO verifies the request. This may involve cross-checking with government records such as death certificates or conducting field inquiries for shifted residences. Without proper verification, a voter’s name cannot be deleted.
Safeguards Against Misuse
Since Form-7 deals with removal rather than addition of names, it carries risk of wrongful deletion. Safeguards include:
-
Notifying the concerned voter before deletion.
-
Allowing objections if the voter disputes the request.
-
Monitoring unusual patterns such as bulk online submissions from the same IP address.
Citizen’s Role
Citizens should regularly check their voter status, especially before elections. If a name is wrongly deleted, the voter can reapply for inclusion through Form-6. This self-checking process helps protect against wrongful disenfranchisement.
Difference from Other Forms
-
Form-6: Used to add a new voter or include someone who has shifted residence.
-
Form-7: Used to remove names due to death, migration, or ineligibility.
-
Form-8: Used to correct details or update personal information.
Outcome
If the verification is successful, the voter’s name is removed from the electoral roll of that constituency. If the request is found invalid, it is rejected and the voter remains on the list.
| Aspect | Details |
|---|---|
| Purpose | Form-7 is used to request the deletion or objection of a name from the electoral roll. |
| Who Can File | Any voter, a relative of the voter, or an authorized person can file it. |
| Grounds for Deletion | Death of the voter, shifting of residence outside the constituency, or duplication of entries. |
| Submission Mode | Available online via NVSP and VHA apps, and offline at Electoral Registration Offices. |
| Verification | Electoral Registration Officers (EROs) must verify documents and objections before approving deletion. |
| Safeguards | Public notices, hearings, and document checks are required to prevent wrongful deletions. |
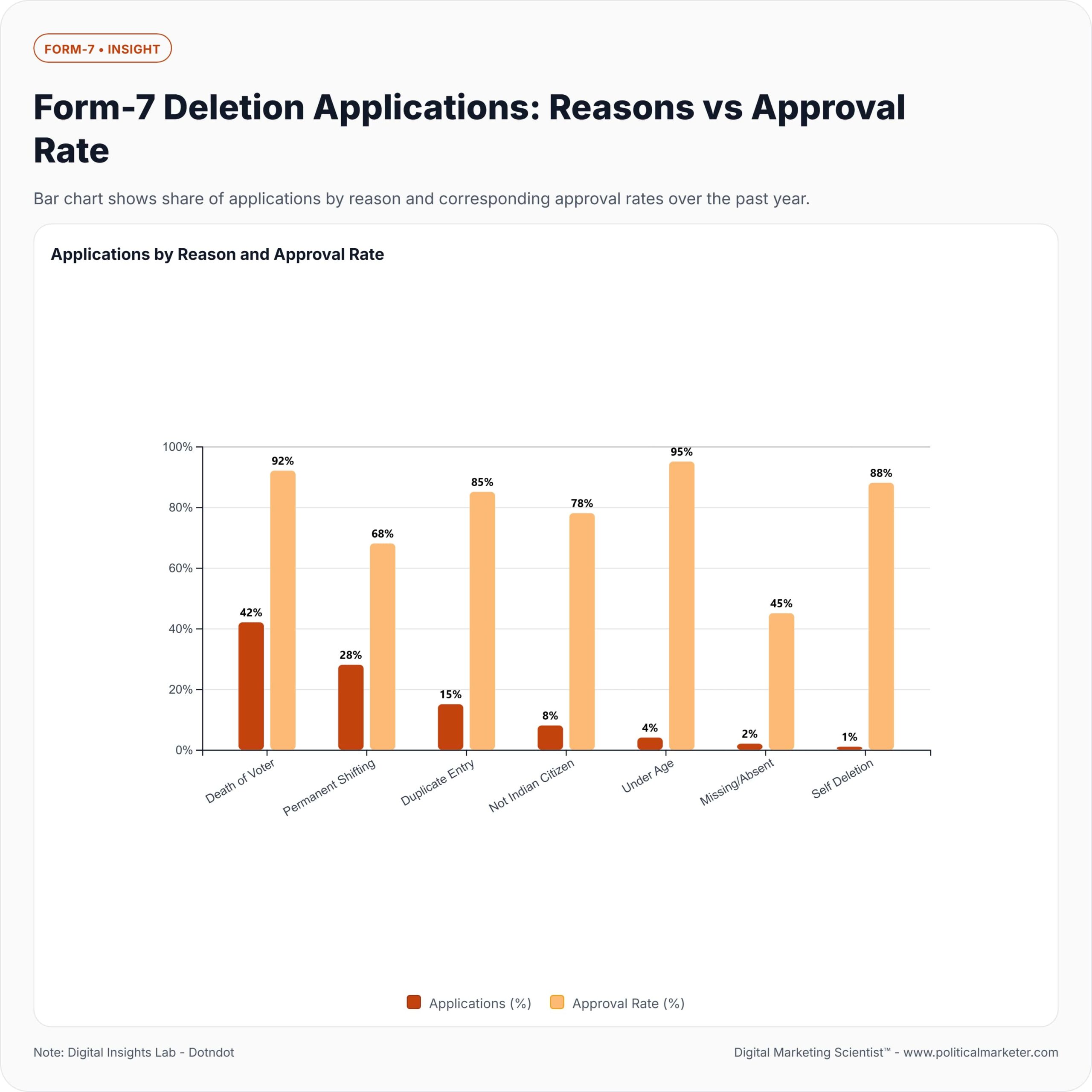
How to Quickly Detect Misuse of Form-7 Deletions
Misuse of Voter ID Form-7 can be spotted by monitoring unusual patterns in deletion requests. Red flags include bulk submissions from the same IP address, duplicate requests targeting the same voters, sudden spikes in deletion activity in specific areas, and repeated “unsuccessful attempts” against particular electors.
Election officials can detect misuse faster by tracking metadata such as timestamps, device IDs, and geographic clusters, while citizens can safeguard themselves by regularly checking their voter status online.
Voter ID Form-7 allows deletion of names from the electoral roll, making it vulnerable to misuse if submitted in bulk against legitimate voters. Detecting such misuse quickly requires systematic checks and real-time monitoring.
The process below explains how election authorities and citizens can identify suspicious patterns.
Purpose of Monitoring
The goal of monitoring Form-7 activity is to ensure that deletions are genuine, such as for deceased or migrated voters, and to prevent wrongful disenfranchisement through fraudulent or politically motivated submissions.
Identifying Suspicious Patterns
Election officials should watch for unusual activity. Key signs include:
-
Large volumes of Form-7 submissions filed within a short period.
-
Multiple requests coming from the same IP address, device, or login credentials.
-
Repeated deletion attempts targeting the same voter or voter group.
-
Unnatural timing of submissions, such as a surge outside working hours.
-
High rates of “unsuccessful attempts” where deletion requests fail due to invalid data.
Use of Metadata
Metadata helps trace misuse within hours. Authorities should analyze IP addresses, timestamps, device IDs, and geographic data.
When several deletion requests cluster around a single booth, ward, or community, it indicates a coordinated attempt rather than routine voter list maintenance.
Verification by Election Registration Officers
Once patterns are flagged, Election Registration Officers (EROs) must verify the authenticity of Form-7 requests.
This includes cross-checking with death records, migration details, or physical verification where necessary. Invalid or duplicate submissions should be rejected immediately to protect voters.
Citizen Safeguards
Citizens play a role by regularly checking their voter status through the National Voter Service Portal (NVSP), Voter Helpline App, or state election websites.
If a wrongful deletion is detected, they can reapply for inclusion using Form-6.
Outcome
By combining metadata analysis, red-flag monitoring, and strict verification, misuse of Form-7 can be detected quickly and contained.
This process ensures electoral rolls remain accurate without compromising the rights of legitimate voters.
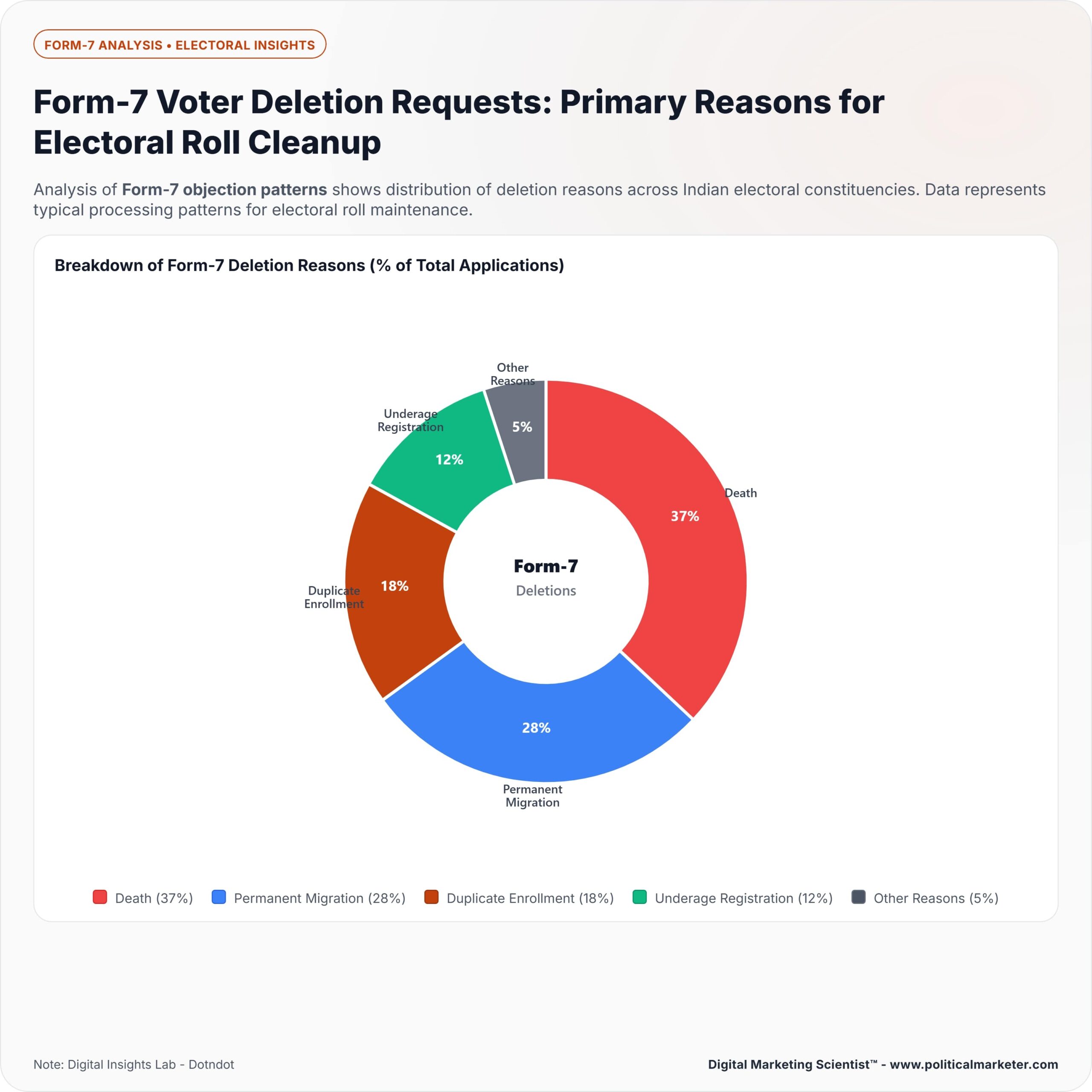
Red Flags That Signal Coordinated Form-7 Voter Deletions
Coordinated misuse of Voter ID Form-7 can be identified through clear warning signs.
These include bulk deletion requests from the same IP address or device, duplicate requests targeting the same voters, sudden spikes in Form-7 activity within specific constituencies, and clusters of requests aimed at particular communities or polling booths.
Unusually high numbers of unsuccessful deletion attempts against the same electors also indicate organized efforts to manipulate voter rolls.
Form-7 deletions, when misused, can remove legitimate voters from the rolls. Detecting coordinated misuse requires looking for patterns that go beyond ordinary voter list corrections.
The process below outlines the major warning signs.
Unusual Volume of Requests
A sudden surge of Form-7 submissions in a short period is a strong indicator of coordinated activity. Large volumes from one constituency or polling booth suggest organized targeting rather than routine corrections.
Common Source of Submissions
Multiple requests originating from the same IP address, device, or user account indicate bulk filing by a single source. Tracking digital fingerprints such as device IDs and login credentials helps detect such clustering.
Duplicate or Repeated Requests
When the same voter is targeted multiple times with deletion requests, it signals intentional misuse. Repeated attempts to delete specific electors should immediately trigger review by the Election Registration Officer (ERO).
Geographic or Community Clusters
Coordinated misuse often focuses on specific wards, minority groups, or politically significant regions. Patterns showing concentrated deletion attempts within a defined area are a clear red flag.
Timing Irregularities
Submission bursts outside normal working hours, such as late-night spikes, suggest automated or centrally managed filing. Election authorities should monitor the timing of requests to detect anomalies.
High Rate of Failed Attempts
A large number of unsuccessful or invalid deletion attempts against the same set of electors points toward a systematic effort to remove them, even if the data provided does not match official records.
Verification Process Triggers
When any of these red flags appear, the ERO must conduct deeper checks before approving deletions. This involves cross-verifying with death records, migration data, and field inquiries to protect voters from wrongful removal.
How Form-7 Differs from Form-6 and Form-8
Form-7 is used to request deletion of a voter’s name from the electoral roll, typically in cases of death, migration, or ineligibility. In contrast, Form-6 is meant for adding new voters or including those who have shifted residence into a new constituency.
Form-8 is used to correct or update voter details such as name, address, age, or photo. Together, these forms cover inclusion, correction, and deletion, but only Form-7 carries the risk of wrongful disenfranchisement, which is why it requires stricter verification.
Form-6, Form-7, and Form-8 serve different purposes in maintaining the accuracy of India’s electoral rolls. Form-6 is used to add a new voter or include someone who has changed residence to a new constituency.
It ensures that eligible citizens are added to the voter list for the first time or after relocation. Form-7, on the other hand, is used to request the deletion of a voter’s name.
This applies in cases where a person has died, permanently shifted out of the constituency, or is otherwise ineligible to remain on that electoral roll.
Since it involves removal, authorities apply stricter checks to prevent wrongful deletion.
Form-8 is designed for correcting or updating voter details, such as name spelling, address, age, or photograph, without affecting the voter’s eligibility.
While Form-6 focuses on inclusion and Form-8 on correction, Form-7 deals with exclusion, which makes its misuse a potential risk to voter rights if not properly verified.
Together, these forms ensure the electoral roll remains comprehensive, accurate, and up to date.
Purpose of Form-6
Form-6 is used to add a new voter to the electoral roll. It applies to citizens who turn 18, first-time voters, or those who have shifted residence and need to be enrolled in a new constituency.
The form ensures that eligible individuals are included in the voter list without delay.
Purpose of Form-7
Form-7 is used to request deletion of a voter’s name from the electoral roll. This applies when a person has died, permanently moved to another constituency, or is otherwise no longer eligible.
Because it involves exclusion rather than inclusion, Form-7 carries higher risk of misuse, and election authorities must verify each request carefully to prevent wrongful disenfranchisement.
Purpose of Form-8
Form-8 is designed for corrections or updates in voter details.
It allows voters to fix errors in name spelling, address, age, or photograph, ensuring the accuracy of their information without affecting their eligibility.
Key Differences
Form-6 focuses on inclusion of new voters. Form-7 deals with deletion of ineligible names.
Form-8 handles corrections and updates. Together, they balance the electoral roll by adding eligible voters, removing ineligible entries, and ensuring accurate records.
Among them, Form-7 requires stricter scrutiny since misuse can remove legitimate voters from the rolls.
| Form | Purpose | Who Can Apply | Key Action |
|---|---|---|---|
| Form-6 | To apply for inclusion of name in the electoral roll (new voter registration or shifting constituency). | Citizens aged 18+ or voters who have changed their constituency. | Addition of new voter. |
| Form-7 | To request deletion or objection to a name in the electoral roll. | Any voter, a relative, or authorized person. | Deletion of name due to death, migration, or duplication. |
| Form-8 | To correct details in the electoral roll (name, photo, age, address, gender, etc.). | Existing registered voters. | Correction or update of voter details. |
Can Citizens Really Delete Votes Online via Form-7?
Citizens can submit Form-7 online through the National Voter Service Portal (NVSP), Voter Helpline App, or GARUDA platform to request deletion of a voter’s name.
However, no name is removed automatically. The Election Registration Officer verifies each request by checking supporting records or conducting field inquiries.
Only after this verification is a voter’s name deleted, ensuring that wrongful or malicious submissions do not directly affect the electoral roll.
Submission Process
Citizens can submit Form-7 online using the National Voter Service Portal (NVSP), the Voter Helpline App, or the GARUDA platform. They must provide voter details and specify the reason for deletion, such as death, migration, or ineligibility.
Verification by Authorities
Once a request is filed, the ERO reviews it. The officer cross-checks records, which may include death certificates, proof of address change, or field verification. Without this step, no deletion is approved. This safeguard prevents wrongful removal of legitimate voters.
Safeguards Against Misuse
To avoid misuse, the system records metadata such as IP addresses and timestamps of submissions. Voters are also notified if a deletion request is filed against their name, allowing them to object before final removal.
Citizen’s Role in Protection
Citizens should monitor their voter status regularly on NVSP or state election portals. If their name is wrongly deleted, they can reapply for inclusion using Form-6. This self-check ensures their voting rights remain intact.
Outcome
Citizens can request deletions online through Form-7, but they cannot delete votes directly. The final decision rests with the ERO after proper verification, striking a balance between maintaining accurate rolls and protecting voters from fraudulent removal.
What Are “Unsuccessful Attempts” to Delete Electors via Form-7?
Unsuccessful attempts to delete electors through Form-7 occur when a submitted deletion request fails verification and is rejected by the Election Registration Officer (ERO).
These attempts are logged within the system and play an important role in identifying suspicious activity.
Reasons for Failure
Requests often fail because of incorrect or incomplete voter details, such as mismatched names, wrong voter ID numbers, or invalid addresses.
They may also be rejected if the applicant provides insufficient proof of death or migration.
In other cases, the ERO may dismiss a request if field verification shows that the voter continues to live in the constituency and remains eligible.
Administrative Review
When an application is marked as unsuccessful, the ERO ensures that the voter’s name remains on the electoral roll.
This review step protects legitimate voters from being wrongfully deleted and preserves the accuracy of the voter list.
Indicators of Misuse
A high number of unsuccessful attempts targeting the same voters or communities can signal coordinated misuse.
Repeated failed requests may suggest deliberate efforts to remove eligible voters by overwhelming the system with false claims.
Election authorities track these patterns to detect and stop such activities.
Monitoring and Accountability
By recording unsuccessful attempts, the system creates an audit trail.
This enables officials to identify users or IP addresses responsible for suspicious submissions and take corrective action if misuse is detected.
It also reassures voters that fraudulent requests cannot directly strip them of their rights without verification.
How Should EROs Verify Bulk Online Form-7 Submissions Quickly?
Election Registration Officers (EROs) are responsible for ensuring that Form-7 requests for deletion are genuine. When bulk submissions arrive online, they must apply systematic checks to protect voter rolls while working efficiently.
Screening for Metadata Patterns
EROs should begin by reviewing digital metadata linked to the submissions. Requests coming from the same IP address, device, or user account within short time frames indicate possible coordinated activity. Identifying these clusters allows officers to prioritize high-risk batches for deeper review.
Cross-Checking with Official Records
Each request should be compared with available government data. For cases citing death, EROs can match details with municipal death records. For migration-related requests, they can review address change records, utility data, or recent voter registrations in other constituencies. This approach eliminates requests filed with false or incomplete information.
Duplicate and Repetitive Request Analysis
Bulk submissions often include duplicate requests against the same voters. EROs should use automated filters to detect such repetition, ensuring that the same elector is not reviewed multiple times. This saves time and exposes attempts to target specific individuals or communities.
Field Verification for Suspicious Clusters
Where unusual deletion clusters are detected, EROs can direct Booth Level Officers (BLOs) to conduct rapid field verification. Visiting a sample set of addresses within the affected area confirms whether the voters continue to reside there. If most are found eligible, the remaining requests from the cluster can be rejected quickly.
Use of Automated Dashboards
Digital dashboards can help EROs track submissions in real time. Features such as flagging unusual spikes, comparing deletion patterns across constituencies, and highlighting high-volume requesters allow quick decision-making.
Communication with Voters
Before deletion, affected voters should be notified by SMS, postal notice, or online alerts. Providing an opportunity to object ensures that genuine electors are not removed without their knowledge. This step also discourages malicious actors, since voters can counter false deletion attempts.
Accountability and Audit Trail
EROs should maintain logs of bulk verification actions. Tracking rejected requests, identifying repeat offenders, and escalating suspicious activity for legal review creates accountability. These audit trails help election authorities respond to misuse systematically and strengthen trust in the verification process.
What Quick Checks Catch Duplicate Form-7 Requests in Minutes?
Duplicate Form-7 submissions are a common sign of misuse, especially during coordinated attempts to remove legitimate voters. Detecting them quickly requires applying systematic checks that can filter out repetition within minutes.
Matching Voter ID Numbers
The fastest check is to compare the unique voter ID number (EPIC). When multiple Form-7 requests target the same EPIC within a short timeframe, the system can flag them as duplicates for review.
Cross-Referencing Personal Details
Names, addresses, and dates of birth can be cross-matched across submissions. Even if the EPIC number is mistyped or slightly altered, identical demographic details will reveal duplicate targeting of the same individual.
IP and Device Tracking
Requests submitted from the same IP address or device within narrow time windows indicate bulk attempts. Identifying clusters of identical or similar requests from one digital source helps catch duplicates rapidly.
Time-Stamp Analysis
Unnatural patterns, such as dozens of requests for the same voter filed within minutes, show deliberate duplication. Reviewing time-stamp data across submissions highlights these irregularities.
Automated Deduplication Filters
Election management systems can run automated scripts to filter out multiple requests linked to the same voter. Deduplication rules can be applied in real time, allowing Election Registration Officers to focus only on unique and potentially valid cases.
Flagging Community-Wide Patterns
If duplicates appear across voters in a single polling booth or community cluster, it suggests targeted deletion attempts. Flagging such patterns prevents large-scale misuse before wrongful removals take place.
By combining voter ID checks, demographic cross-referencing, metadata analysis, and automated filters, election officials can detect duplicate Form-7 requests within minutes and stop manipulation attempts before they affect the rolls.
How to Spot Form-7 Deletion Bursts from Single IP Addresses
Coordinated misuse of Form-7 often involves multiple deletion requests filed in quick succession from a single IP address. Detecting such bursts requires a mix of technical monitoring and structured verification.
Monitoring Submission Logs
Election systems should capture detailed submission logs, including IP addresses, device identifiers, and timestamps. Reviewing these logs reveals whether multiple requests originate from the same digital source within a narrow time frame.
Identifying Unusual Spikes
An abnormal surge of deletion requests from one IP address within minutes or hours is a red flag. Normal voter behavior spreads across different devices and timings, while misuse shows concentrated spikes.
Cross-Referencing with Voter Data
When many requests from one IP target voters within the same polling booth, ward, or community, it signals an organized attempt rather than genuine submissions. Linking submission metadata with voter roll data helps confirm patterns of manipulation.
Using Automated Alerts
Election authorities can configure automated alerts to flag high-frequency submissions from identical IP addresses. Thresholds, such as more than ten requests within a five-minute window, allow real-time detection without waiting for manual audits.
Filtering Duplicate Attempts
Bursts often include repeated or duplicate requests against the same voters. Automated deduplication tools can identify and isolate these attempts for quick review, preventing wrongful deletion from progressing further.
Escalating for Verification
Once a burst is detected, Election Registration Officers should verify a sample of the targeted voters through field checks or supporting documents. If voters are still eligible, the batch of suspicious requests can be rejected collectively.
By combining log monitoring, spike detection, metadata analysis, and automated alerts, election officials can quickly identify Form-7 deletion bursts from single IP addresses and protect electoral rolls from manipulation.
Which Metadata Helps Detect Form-7 Misuse Within Hours
Metadata captured during online Form-7 submissions provides early warning signs of misuse. When monitored effectively, it allows election authorities to detect suspicious activity within hours instead of waiting for manual reviews.
IP Address Tracking
IP addresses reveal the origin of submissions. Multiple requests from the same IP within a short time indicate possible bulk activity. Identifying such clusters helps flag coordinated attempts to delete voters.
Device Identifiers
Unique device fingerprints, such as browser type, operating system, or device ID, allow detection of repeated submissions from a single device. Even when IP addresses change, device metadata exposes concentrated activity.
Timestamp Analysis
Time-based patterns highlight abnormal bursts. A sudden wave of requests filed within minutes or at unusual hours, like late night or early morning, suggests automated or centrally managed filing.
User Account Data
Online submissions often require login through NVSP or linked accounts. Reviewing which accounts submit high volumes of requests provides insight into suspicious actors who may be filing deletions beyond reasonable limits.
Geographic Markers
Metadata linked to geolocation can show if requests supposedly affecting one constituency are filed from distant or unrelated locations. This mismatch points to misuse rather than genuine local submissions.
Request History Logs
Comparing current requests with past activity exposes repeated attempts against the same voters. Logs showing multiple unsuccessful or duplicate submissions strengthen the evidence of targeted manipulation.
By analyzing IP data, device identifiers, timestamps, user accounts, geolocation markers, and request history, election officers can identify misuse patterns early and protect voters from wrongful deletions.
How Do NVSP, VHA, and GARUDA Apps Handle Form-7 Flows
Form-7 requests for deletion of voter names can be submitted through three official platforms: the National Voter Service Portal (NVSP), the Voter Helpline App (VHA), and the GARUDA application. Each platform follows a structured flow to capture details, validate inputs, and route the request to the Election Registration Officer (ERO) for verification.
NVSP Portal
The NVSP provides a web-based interface where citizens log in with credentials and submit Form-7. The portal collects details such as voter ID number, personal information, and the reason for deletion.
Once the form is submitted, the system generates an acknowledgment number, allowing applicants to track the request. NVSP also forwards the request to the respective constituency’s ERO for verification.
Voter Helpline App (VHA)
The VHA offers a mobile-first experience for filing Form-7. It allows users to enter voter details, upload supporting documents such as a death certificate or address proof, and submit requests directly from a smartphone.
The app integrates notifications, sending alerts about the status of the application, objections raised, or completion of verification. This real-time communication ensures voters are informed if a deletion request is filed against their name.
GARUDA App
The GARUDA application is primarily designed for election officials but also processes voter-related submissions, including Form-7. It captures metadata such as GPS location, device details, and timestamps of the request.
This data helps election authorities detect suspicious activity like bulk deletions filed from a single source. GARUDA’s structured backend flow supports EROs and Booth Level Officers (BLOs) by providing dashboards for monitoring and verifying submissions efficiently.
Verification Across Platforms
Regardless of whether a Form-7 request is submitted via NVSP, VHA, or GARUDA, the system routes the request to the ERO. The officer cross-checks records, issues notices to the concerned voter, and conducts field inquiries if needed.
Only after this verification does the deletion proceed.
Safeguards in Digital Flows
All three platforms incorporate audit trails, unique acknowledgment IDs, and metadata logging. These safeguards prevent unauthorized deletions and enable authorities to trace back suspicious submissions to their origin.
By combining citizen-facing portals (NVSP and VHA) with the official GARUDA system, the Election Commission ensures that the Form-7 process remains transparent and verifiable.
What Is the Fastest Workflow to Audit Form-7 Requests
Auditing Form-7 requests requires a balance of speed and accuracy to ensure legitimate deletions while preventing misuse. The fastest workflow involves combining automated system checks with targeted manual verification.
Automated Metadata Screening
All incoming Form-7 submissions should be scanned automatically for metadata such as IP addresses, device identifiers, timestamps, and geolocation. This allows early detection of bulk requests or suspicious patterns like multiple submissions from a single source.
Duplicate and High-Volume Filtering
The system should immediately flag duplicate requests against the same voter ID or clusters of requests within the same polling booth.
Automated filters can separate unique cases from repetitive or bulk attempts, reducing the workload for manual review.
Cross-Verification with Databases
Validating each request against government records speeds up the process. For death-related deletions, cross-check with municipal death registers. For migration claims, check utility data or recent voter roll additions in other constituencies.
Linking Form-7 data with official records reduces reliance on lengthy field inquiries.
Priority-Based Queueing
Requests should be sorted into priority levels. High-risk batches, such as those from a single IP or involving community clusters, require immediate review. Low-risk requests with verifiable supporting documents can move through faster approval queues.
Randomized Field Verification
For suspicious or high-volume requests, Booth Level Officers (BLOs) can conduct rapid field checks on a sample of cases. If the majority are found invalid, the entire cluster can be flagged for rejection, saving time and resources.
Citizen Notification System
Applicants and affected voters should receive real-time alerts through SMS, email, or the Voter Helpline App. This ensures transparency and gives voters an opportunity to object before a name is deleted.
Continuous Monitoring Dashboards
ERO offices should use dashboards that provide real-time analytics on submissions, showing spikes, rejection rates, and geographic patterns. These tools allow officers to act within hours instead of waiting for manual reports.
By integrating automated screening, cross-verification with official records, and targeted field checks, EROs can audit large volumes of Form-7 requests quickly while maintaining voter protection.
Can OTP and Phone Logs Reveal Form-7 Manipulation Quickly
Form-7 submissions require authentication, and the use of One-Time Passwords (OTPs) linked to mobile numbers provides a traceable layer of accountability. Reviewing OTP records and phone logs can expose patterns of misuse within hours.
OTP Authentication Tracking
Each Form-7 request generates an OTP sent to the registered mobile number of the applicant. If multiple requests originate from the same phone number, it indicates possible coordinated misuse. Monitoring OTP usage patterns helps detect bulk filings quickly.
Phone Number Repetition
When the same mobile number is repeatedly used across several deletion requests targeting different voters, it raises suspicion. Linking repeated submissions to single numbers allows officials to trace back to the source of manipulation.
Log Correlation with Metadata
Phone logs, when correlated with IP addresses, device identifiers, and timestamps, provide a clearer picture of activity. For example, if the same phone number is associated with requests from multiple constituencies in a short timeframe, it suggests fraudulent intent.
High-Frequency OTP Requests
Unusually high volumes of OTP generation within a narrow time window signal automated or bulk attempts. This pattern can be flagged by automated systems to trigger immediate review by Election Registration Officers.
Cross-Verification with Voter Data
Officials can match OTP logs with the voter details submitted in Form-7. If the same number is linked to unrelated voters, the request set should be flagged as invalid and reviewed closely.
Preventive Deterrence
Maintaining audit trails of OTP requests and phone numbers creates accountability. Once patterns are identified, authorities can block repeat offenders, reducing the likelihood of further misuse.
By combining OTP authentication logs with metadata and voter records, election authorities can expose coordinated manipulation attempts in the Form-7 process much faster than relying on manual verification alone.
What Did ECI Say About Online Vote Deletions via Form-7
The Election Commission of India (ECI) has clarified its position on online Form-7 submissions to address concerns about wrongful voter deletions.
While citizens can submit deletion requests through online platforms such as the National Voter Service Portal (NVSP), the Voter Helpline App, and GARUDA, the Commission emphasizes that no voter can be removed automatically based on an online request alone.
Verification Requirement
The ECI has stated that every Form-7 request must undergo verification by the Election Registration Officer (ERO). This includes cross-checking with official records, notifying the concerned voter, and in some cases, conducting field verification.
The process ensures that deletion requests cannot bypass scrutiny and directly alter the rolls.
Protection Against Misuse
According to the Commission, online platforms act as submission channels but not as final authority for deletions. The system is designed to flag suspicious activity such as bulk submissions, duplicate requests, or high-frequency attempts from the same IP address or phone number.
These checks are meant to protect legitimate voters from being wrongly removed.
Accountability Measures
The ECI has highlighted that voters receive notifications when a deletion request is filed against their name. This safeguard allows them to raise objections before their entry is removed.
The Commission has also stressed that unsuccessful or duplicate attempts are logged, creating an audit trail that can be reviewed for possible manipulation.
Official Position
In its statements, the ECI has reassured citizens that technology is used to make voter services accessible but not to compromise voter rights. Online Form-7 requests initiate a process, but the final decision rests only after due diligence by election officials.
This balance, according to the Commission, is necessary to maintain both convenience and integrity in the voter registration system.
How Can District SPs Validate Mass Form-7 Filings Promptly
District Superintendents of Police (SPs) play a supporting role in safeguarding electoral integrity when mass Form-7 filings raise suspicion of manipulation. Their validation efforts focus on detecting fraudulent activity, coordinating with civil authorities, and ensuring public confidence in the process.
Monitoring Digital and Physical Patterns
SPs can request access to metadata analysis from election authorities, including IP addresses, OTP logs, and phone numbers linked to large volumes of Form-7 submissions. When unusual clusters appear, police can cross-check whether these digital traces connect to organized groups or specific actors attempting to influence voter rolls.
Coordinating With Election Officers
Collaboration between SPs, Election Registration Officers (EROs), and Booth Level Officers (BLOs) ensures faster verification. Once suspicious clusters are identified, SPs can deploy personnel to assist BLOs in confirming whether voters listed for deletion are still residing in the constituency.
Field Intelligence and Local Verification
Police networks provide ground intelligence that complements administrative checks. Station House Officers (SHOs) and beat constables can quickly verify whether mass deletions correspond to genuine migration or deaths in their jurisdictions. Their reports allow district authorities to reject fraudulent requests without delay.
Preventing Organized Misuse
If metadata points to a coordinated campaign, SPs can investigate the source of bulk submissions, including cyber units tracing common devices or accounts. Identifying the origin of mass filings helps deter further attempts and allows legal action against those orchestrating fraudulent deletions.
Community Communication
SPs can also support awareness campaigns, ensuring that citizens are informed about wrongful deletion risks. By encouraging voters to check their electoral status regularly and report suspicious activity, they strengthen local oversight.
Through a combination of digital monitoring, inter-agency coordination, field intelligence, and preventive action, district SPs can validate mass Form-7 filings promptly and ensure that electoral rolls remain free from manipulation.
Which Anomaly Patterns in Form-7 Suggest Scripted Submissions
Scripted or automated Form-7 filings can overwhelm electoral systems and attempt mass deletions of legitimate voters. Detecting anomalies in submission patterns is essential to identify these attempts quickly.
Identical Timestamps
When large batches of Form-7 requests are recorded within seconds of each other, it suggests automated scripting rather than individual citizen activity. Natural submissions show variation in timing, while scripts often produce identical or near-identical timestamps.
Repeated IP and Device Usage
A high number of requests from the same IP address or device in a short window indicates central control. Even when IP addresses are rotated through proxies, device fingerprints or browser signatures often remain consistent, exposing automation.
Uniform Data Structures
Scripted requests frequently contain identical formatting errors, repetitive phrases in the reason for deletion, or standardized attachments. These uniformities reveal machine-driven inputs instead of genuine citizen filings.
High Frequency of OTP Requests
Scripts attempting bulk deletions often generate multiple OTPs for the same phone number or cycle through a limited set of numbers. Abnormally high OTP traffic linked to Form-7 activity is a clear red flag.
Geographic Mismatches
Submissions targeting voters in one constituency but originating digitally from distant or unrelated locations show manipulation. Automation often ignores natural geographic alignment between the filer and the constituency.
Duplicate Voter Targeting
Scripted activity commonly generates duplicate or repeated requests against the same voters. These duplication bursts indicate that the system is being stressed by loops in automated filing.
Clustered Community Targeting
When a disproportionate number of Form-7 submissions focus on a single ward, minority group, or polling booth within a very short timeframe, it suggests targeted automation rather than organic requests.
By monitoring timestamp uniformity, IP and device repetition, structured input errors, OTP generation spikes, geographic mismatches, and clustered targeting, election authorities can identify scripted Form-7 submissions and act before they distort voter rolls.
How Do Identical Reasons in Form-7 Deletions Raise Alarms
Form-7 requires applicants to provide a reason for requesting deletion of a voter’s name, such as death, migration, or disqualification. When authorities detect identical reasons repeated across large batches of applications, it signals possible misuse and raises immediate suspicion.
Uniformity Across Submissions
Genuine requests usually vary in wording, reflecting individual circumstances. Identical phrasing across hundreds of applications suggests that the entries were generated centrally, often through scripts or bulk filing, rather than submitted by separate citizens.
Pattern Detection in Language
Authorities monitor for recurring templates, such as the same spelling mistakes, identical justification lines, or copy-pasted explanations. Consistency in language across unrelated cases points to automation or coordinated filing by a single source.
Linking with Metadata
When uniform reasons appear alongside other anomalies like identical IP addresses, common phone numbers, or simultaneous timestamps, the evidence of scripted or organized submissions becomes stronger. Metadata correlation confirms that the deletion drive is not organic.
Targeted Community Impact
Identical reasons often accompany mass deletions from a specific booth, ward, or demographic group. This concentrated targeting raises alarms about voter suppression efforts disguised as legitimate deletions.
Verification Burden
Such patterns place additional workload on Election Registration Officers, who must cross-check whether the claims match official records. For example, mass applications citing “death” can be verified quickly against municipal registers. If many voters are found alive, the batch can be flagged as fraudulent.
Preventive Measures
Flagging identical reasons early allows authorities to pause the processing of suspect batches, issue notices to affected voters, and deploy Booth Level Officers for sample field verification. This prevents wrongful deletions before they reach the electoral roll.
By identifying repeated justifications in Form-7 submissions and linking them with technical and geographic evidence, election authorities can uncover manipulation attempts designed to disenfranchise voters.
What Quick Triage Rules Should EROs Use on Form-7
Election Registration Officers (EROs) handle high volumes of Form-7 submissions, especially during revision periods. Quick triage rules help them separate genuine requests from suspicious ones and ensure timely verification without overloading the system.
Screening by Volume and Source
EROs should immediately flag bulk submissions from the same IP address, device, or login account. Large clusters of requests arriving within short time windows require higher scrutiny compared to single or low-volume filings.
Duplicate Request Identification
Automated filters should detect duplicate or repeated deletion attempts against the same voter ID or demographic details. Such duplication indicates deliberate targeting of specific voters or poorly disguised scripted submissions.
Reason Consistency Review
If hundreds of requests carry identical reasons such as “shifted residence” or “death,” they should be prioritized for deeper checks. Natural filings show variation in explanations, while mass repetition points to coordinated filing.
OTP and Phone Number Analysis
EROs should cross-check OTP and mobile logs. Multiple submissions linked to a single phone number or unusually high OTP generation within a short time suggests misuse.
Geographic Correlation
Requests filed in bulk but targeting voters concentrated in a specific polling booth or ward should be triaged as high-risk. Such clustering often reflects attempts to disenfranchise particular communities.
Cross-Check with Official Records
Deletion requests citing death should be quickly compared with municipal death registers. Those claiming migration can be sampled against utility or residence records. Fast database checks allow early rejection of fraudulent claims.
Field Verification Prioritization
When anomalies are flagged, EROs should assign Booth Level Officers to conduct rapid sample field verification. If most checks in a cluster prove invalid, the remaining requests from that batch can be set aside as suspicious.
By applying these triage rules, volume screening, duplicate detection, reason review, OTP analysis, geographic clustering, record validation, and targeted field checks, EROs can quickly prioritize which Form-7 requests need immediate attention while protecting genuine voters from wrongful deletion.
Can Geo-Location of Phones Expose Form-7 Fraud Indicators
Geo-location data from mobile phones linked to Form-7 submissions can reveal irregularities that point to fraudulent activity. When combined with metadata such as IP addresses and OTP logs, location insights help election officials detect patterns that would otherwise remain hidden.
Detecting Remote Submissions
If large numbers of Form-7 requests for deletions in one constituency originate from phones located far outside the area, it suggests that the submissions were not filed by genuine local residents. This mismatch highlights attempts to manipulate rolls remotely.
Identifying Centralized Filing
When multiple phones linked to submissions show the same or nearby geo-coordinates, such as cybercafés or rented offices, it indicates centralized filing. This pattern is different from natural distribution across households in a constituency.
Linking Suspicious Clusters
Geo-location data helps track whether deletion requests disproportionately target voters from specific booths or wards, while being filed from unrelated geographic zones. Such clustering is a strong indicator of organized campaigns aimed at selective voter removal.
Cross-Referencing with Timing
Geo-location becomes more valuable when correlated with timestamps. Dozens of requests submitted within minutes from the same location, targeting voters across different constituencies, reveal scripted filing rather than individual citizen actions.
Supporting Field Verification
When flagged patterns emerge, geo-location data allows Election Registration Officers to direct Booth Level Officers for targeted field checks in affected areas. This speeds up the process of confirming whether the voters listed for deletion are genuine residents.
Preventing Repeat Offenses
By maintaining logs of geo-coordinates tied to suspicious filings, election authorities can identify hotspots of misuse and monitor them more closely during future revision cycles. This proactive approach prevents repeat manipulation.
Using geo-location data alongside other digital markers gives election authorities a powerful tool to uncover fraud indicators in Form-7 submissions and protect eligible voters from wrongful deletions.
How to Compare Form-7 Spikes Across Constituencies for Patterns
Form-7 spikes are indicators of unusual deletion activity that may point to coordinated manipulation. Comparing them across constituencies helps detect broader patterns beyond isolated cases. Election officials can use both quantitative and qualitative checks to establish whether the spikes are organic or scripted.
Establishing Baseline Trends
Authorities should first analyze historical data for each constituency to understand normal Form-7 volumes. Seasonal increases, such as during voter roll revisions, serve as a benchmark. Any spike that exceeds this baseline disproportionately is worth deeper review.
Cross-Constituency Volume Analysis
Comparing the number of Form-7 submissions across multiple constituencies during the same period highlights anomalies. For example, if one constituency records 10 times more deletions than its neighbors with similar demographics, it suggests an engineered surge.
Timing Synchronization
If several constituencies experience spikes within the same narrow time window, it indicates a centrally managed effort. Reviewing submission timestamps across districts helps determine whether these spikes were coincidental or part of a coordinated campaign.
Source and Metadata Comparison
Officials should compare IP addresses, device fingerprints, and phone numbers across constituencies. If identical sources appear in multiple areas, it shows that the same actors are filing mass deletions across different rolls.
Reason Consistency Across Batches
Patterns emerge when large clusters in multiple constituencies cite the same deletion reason, such as “shifted residence,” using identical language. Such uniformity points to scripting rather than genuine voter-initiated requests.
Geographic Targeting Review
Cross-constituency comparison should also include mapping which booths or wards were targeted. If minority-dominated or politically significant areas across constituencies show disproportionate deletions, it highlights selective targeting.
Dashboard-Based Monitoring
Digital dashboards can be designed to track Form-7 submissions in real time across constituencies. Visual tools such as heat maps, spike graphs, and cluster comparisons allow faster identification of irregularities that would otherwise remain hidden in raw data.
By applying these comparison methods baseline checks, volume analysis, timing reviews, metadata matching, reason uniformity, and geographic mapping authorities can uncover coordinated Form-7 patterns that extend beyond a single constituency and protect voters from large-scale disenfranchisement.
What Timeline Best Practices Prevent Rash Form-7 Deletions
Timely management of Form-7 requests is critical to prevent wrongful voter deletions. A structured timeline ensures that each request goes through adequate verification without unnecessary delays or rushed decisions.
Minimum Verification Period
Election authorities should maintain a mandatory verification period before approving deletions. This window allows Election Registration Officers (EROs) to cross-check records, notify affected voters, and conduct field inquiries if required. Immediate deletions without this buffer risk disenfranchising eligible voters.
Staggered Processing of Bulk Requests
When bulk Form-7 applications are received, they should be processed in batches rather than cleared all at once. Staggered handling gives officials time to identify anomalies such as duplicate requests, identical reasons, or suspicious metadata.
Notification Timeline for Voters
Voters should be notified promptly when a deletion request is filed against their name. A defined period, such as seven days, should be provided for objections or clarifications. This timeline ensures that citizens have a fair chance to contest wrongful deletions.
Synchronization With Revision Cycles
Form-7 processing should align with scheduled voter list revisions. Deletions processed too close to election dates reduce the ability of voters to challenge them. Setting cut-off dates well before the final roll publication prevents last-minute manipulation.
Escalation of High-Risk Cases
Applications flagged through metadata analysis or bulk filing patterns should follow an extended verification timeline. These cases should remain pending until Booth Level Officers confirm voter status through sample field checks.
Regular Review Intervals
EROs should review pending Form-7 cases at fixed intervals using digital dashboards. Weekly or bi-weekly reviews help track progress and prevent accumulation of unverified requests that may later be processed hastily.
By enforcing mandatory verification windows, staggering bulk submissions, setting clear voter notification periods, aligning deletions with revision cycles, and escalating suspicious cases, election authorities can prevent rash Form-7 deletions and protect the accuracy of electoral rolls.
What Safeguards Stop Centralized Software Abuse of Form-7
Centralized software misuse occurs when automated tools or coordinated platforms submit large numbers of Form-7 applications to manipulate voter rolls. To counter this, election systems and officials must enforce layered safeguards that restrict bulk automation while protecting legitimate citizen requests.
Authentication Controls
Every Form-7 submission requires mobile-based OTP verification linked to a valid number. Tracking OTP logs ensures that the same number cannot generate high volumes of requests without being flagged. This authentication step limits mass filing by automated scripts.
Metadata Monitoring
Systems should log IP addresses, device identifiers, and timestamps for each submission. Large clusters of requests from a single IP or device within narrow intervals must trigger automatic red flags. This monitoring makes it difficult for centralized software to hide its activity.
Request Rate Limiting
Platforms such as NVSP, Voter Helpline App, and GARUDA should enforce limits on the number of requests allowed per user account or device in a set time. By throttling excessive submissions, the system can block automated bulk filings at the source.
Duplicate and Pattern Detection
Automated scripts often generate uniform requests, with identical reasons, repeated formats, or duplicate targeting of the same voters. Built-in algorithms that scan for duplication and repetitive language help isolate batches likely generated by software.
Escalation Protocols
Once a suspicious batch is detected, Election Registration Officers (EROs) can halt processing until further verification is completed. Booth Level Officers may be directed to conduct sample field checks, while technical teams review the digital trail for abuse.
Voter Notification Safeguards
Notifications sent to affected voters by SMS, email, or postal notice ensure that fraudulent deletions cannot bypass citizen awareness. Even if automated submissions are filed, voters have the opportunity to raise objections before their names are removed.
Legal and Enforcement Backing
Suspicious activity traced to centralized filing operations should be escalated to cybercrime units. Maintaining audit trails of IPs, OTPs, and device metadata enables investigation and deters repeated abuse.
Through layered authentication, metadata monitoring, request throttling, duplication checks, escalation protocols, voter notifications, and enforcement action, the election system can effectively prevent centralized software from abusing Form-7 deletions.
How Did ECI’s Fact-Check Address Form-7 Deletion Claims
The Election Commission of India (ECI) issued a fact-check after claims circulated that online Form-7 submissions were leading to mass, unchecked deletions of voters from electoral rolls. The Commission clarified the process and emphasized safeguards built into the system.
Clarifying the Role of Online Platforms
The ECI stated that the National Voter Service Portal (NVSP), the Voter Helpline App (VHA), and the GARUDA platform are only channels for submitting Form-7 requests. These platforms do not automatically remove names but forward the applications to the concerned Election Registration Officer (ERO) for verification.
Verification as a Mandatory Step
The Commission highlighted that no voter is deleted solely based on an online submission. Every Form-7 request must be verified by the ERO through official records, field inquiries, and notices issued to the concerned voter. Without this due process, no deletion can take place.
Addressing Claims of Mass Deletions
The fact-check specifically countered allegations that thousands of voters were being dropped from rolls without scrutiny. The ECI explained that spikes in Form-7 filings are logged and reviewed, and patterns suggesting bulk misuse are flagged for deeper investigation.
Safeguards Highlighted by the Commission
The ECI underscored safeguards such as voter notifications through SMS or post, metadata analysis of online submissions, and audit trails that record unsuccessful and duplicate attempts. These measures ensure transparency and prevent wrongful disenfranchisement.
Reassurance to Voters
In its statement, the Commission reassured citizens that their names cannot be removed without their knowledge. If a deletion request is filed, the voter has the right to object within a notified period before any final decision is taken.
Through its fact-check, the ECI reinforced that Form-7 deletions are not automated outcomes of online activity but regulated decisions that require human verification, thereby dismissing claims of arbitrary voter removal.
Can Public Dashboards Show Real-Time Form-7 Anomalies Safely
Public dashboards can enhance transparency by showing trends in Form-7 submissions, but they must balance openness with data security. Properly designed dashboards reveal patterns without exposing sensitive voter details.
Aggregated Data Display
Dashboards should present data at an aggregated level, such as total Form-7 requests per constituency, daily spikes, or percentage changes. Showing only summary-level statistics prevents misuse of individual voter information while still alerting the public to unusual activity.
Anomaly Indicators
Visual indicators like graphs or heat maps can highlight sudden increases in deletion requests, duplicate patterns, or suspicious clusters in specific areas. By signaling anomalies without revealing personal data, dashboards make oversight safer.
Privacy Protections
No personally identifiable information, such as names, voter IDs, or phone numbers, should appear on public dashboards. Instead, the system should restrict access to detailed data for Election Registration Officers (EROs) and authorized officials only.
Real-Time Monitoring Features
Dashboards can update in real time with anonymized metadata trends, such as the number of requests from a single IP or the proportion of applications citing identical reasons. These trends help stakeholders detect manipulation without compromising individual privacy.
Accountability Layer
Making such dashboards public ensures that political parties, civil society, and media can monitor voter roll changes. This external oversight reduces the chances of wrongful deletions going unnoticed.
Controlled Access for Investigations
While public dashboards focus on summary data, advanced investigative dashboards with deeper metadata insights can remain restricted to election officials. This layered approach ensures transparency for citizens and operational control for administrators.
By combining aggregated statistics, anomaly visualization, strict privacy rules, and tiered access levels, public dashboards can safely display real-time Form-7 anomalies and strengthen confidence in the electoral process.
What Documentation Should Accompany Each Form-7 to EROs
For Election Registration Officers (EROs) to verify Form-7 requests effectively, each application must include supporting documentation that justifies the deletion. Proper documentation reduces fraudulent attempts and speeds up the verification process.
Identity Proof of Applicant
The person submitting Form-7 should attach proof of their identity, such as a voter ID card, Aadhaar card, or another government-issued photo ID. This ensures that the request is traceable to a genuine individual and not submitted anonymously.
Proof of Reason for Deletion
Each deletion reason requires specific supporting evidence:
-
In case of death: A municipal death certificate, hospital-issued death record, or other official confirmation.
-
In case of migration: Address proof showing residence in a new constituency, such as utility bills, rental agreements, or government records.
-
In case of disqualification: Relevant legal documents that confirm loss of eligibility, such as court orders.
Voter Details of the Person Targeted for Deletion
The application must include the Electors Photo Identity Card (EPIC) number, name, age, and address of the voter whose name is sought to be deleted. Providing these details avoids ambiguity and prevents wrongful targeting of unrelated individuals.
Contact Information of Applicant
Form-7 submissions should carry the applicant’s phone number or email ID. This allows the ERO to contact them for clarification during verification and helps establish accountability.
Declaration by the Applicant
A signed declaration confirming the accuracy of the details should be attached. This statement makes the applicant legally accountable if the request is found to be false or malicious.
System-Generated Acknowledgment
For online submissions via NVSP, Voter Helpline App, or GARUDA, the acknowledgment slip generated by the system should accompany the request. This record helps both applicants and officials track the progress of the case.
Supporting Metadata for EROs
Along with documents, the digital submission should carry metadata such as IP address, timestamp, and OTP verification logs. These markers provide EROs with additional context for spotting anomalies in bulk submissions.
By requiring identity proof, specific supporting documents, complete voter details, applicant contact information, signed declarations, and system metadata, EROs can evaluate Form-7 requests quickly while ensuring transparency and accountability.
How Does Special Intensive Revision Interact with Form-7
The Special Intensive Revision (SIR) is a structured exercise conducted by the Election Commission of India to update electoral rolls. During this period, applications under Form-6, Form-7, and Form-8 are processed in bulk to ensure that the voter list remains accurate ahead of elections. Form-7, which deals with deletions, plays a key role in this revision cycle.
Integration with the Revision Schedule
During SIR, citizens, political parties, and officials can submit Form-7 applications to request deletion of names of voters who have died, migrated, or become ineligible. These requests are accepted alongside applications for inclusion (Form-6) and corrections (Form-8). The timeline ensures that all changes are considered before the final publication of rolls.
Verification Standards During SIR
Since Form-7 carries the risk of wrongful deletions, EROs apply stricter checks during the revision process. Each application is verified against official records, and notices are issued to the concerned voters. The SIR framework gives officers additional time to investigate bulk submissions that appear suspicious.
Bulk Pattern Monitoring
Large-scale deletions are more visible during SIR because of real-time dashboards and comparative tracking across constituencies. Spikes in Form-7 submissions from certain areas are flagged immediately, allowing for closer scrutiny. This helps detect organized attempts to manipulate rolls.
Role of Booth Level Officers
BLOs are heavily involved in SIR. They conduct door-to-door verification in cases where Form-7 deletions are concentrated in a booth or ward. Their reports help confirm whether voters still reside in the area or whether the deletion requests are invalid.
Safeguard of Objection Period
As part of SIR, the Election Commission provides a defined period for objections. Voters are informed if a deletion request is filed against them, giving them an opportunity to contest it before any action is taken. This safeguard reduces the risk of wrongful disenfranchisement.
Publication and Transparency
All accepted deletions through Form-7 during SIR are reflected in draft electoral rolls. Citizens, political parties, and civil groups can review these drafts and raise objections, ensuring public oversight.
Through its integration into the Special Intensive Revision, Form-7 is not only processed systematically but also monitored under stricter checks, balancing the need for accurate rolls with protection against fraudulent deletions.
Which Threshold Triggers Automatic Review of Form-7 Clusters
Form-7 clusters often signal attempts to manipulate voter rolls, especially when multiple deletion requests appear within a short time. Automatic review thresholds help Election Registration Officers (EROs) detect and investigate such activity before wrongful deletions occur.
Volume-Based Thresholds
A cluster of more than 20 to 25 Form-7 requests from the same polling booth within a single day should trigger an automatic review. In larger constituencies, higher thresholds such as 100 or more in a week can be applied. These limits are designed to separate natural voter list corrections from unusual surges.
Source-Based Thresholds
When 10 or more requests originate from the same IP address, device, or phone number within an hour, the system should flag the cluster for investigation. Such concentrated submissions strongly indicate centralized or automated filing.
Duplicate Request Thresholds
If the same voter is targeted with two or more Form-7 requests within a short timeframe, the system should trigger an alert. Duplicate targeting is a classic indicator of misuse intended to overwhelm verification processes.
Geographic Concentration Thresholds
Clusters where over 15 percent of voters from a single booth or ward are marked for deletion in one revision cycle should be escalated. This level of concentration suggests that specific communities or areas are being selectively targeted.
Timing Anomalies
Thresholds should also apply to unnatural submission patterns. For example, a burst of more than 50 requests filed late at night or during non-working hours should be flagged for automated review, as genuine citizen activity typically shows more dispersed timing.
Automated Dashboard Alerts
Election systems can integrate these thresholds into real-time dashboards. When a threshold is crossed, the dashboard should immediately notify EROs, prompting faster verification by Booth Level Officers and temporary suspension of the suspicious batch until validated.
By setting clear thresholds based on volume, source, duplication, geography, and timing, election authorities can automatically trigger reviews of Form-7 clusters and prevent wrongful voter deletions.
How Do Rate-Limits Reduce Bot-Like Form-7 Submissions Online
Rate-limiting is one of the most effective safeguards against automated or bot-driven attempts to misuse Form-7 for voter deletions. By controlling how many requests can be submitted within a given period, the system filters genuine citizen activity from suspicious mass submissions.
Controlling Submission Frequency
Rate-limits set caps on how many Form-7 requests a single IP address, device, or user account can submit in a defined window, such as five per hour or twenty per day. This prevents automated software from flooding the system with hundreds of deletion requests in minutes.
Detecting Abnormal Spikes
When rate-limits are breached, the system generates alerts for Election Registration Officers (EROs). These alerts identify potential misuse patterns, such as multiple requests originating from the same device within seconds, which mirrors bot-like behavior.
Preventing Bulk Automation
Bots typically rely on high-speed, repetitive submissions. By slowing down the allowed request flow, rate-limiting disrupts automation scripts. This forces each submission to mimic normal human behavior, making fraudulent campaigns more difficult and easier to detect.
Protecting System Stability
Large-scale automated requests can overload election servers and slow down processing for genuine users. Rate-limiting ensures the system remains available to citizens while filtering abusive traffic from software-driven campaigns.
Layered Enforcement
Rate-limits can be applied at multiple levels: per IP address, per device ID, per registered mobile number, and per session. Combining these layers ensures that attackers cannot bypass restrictions simply by switching devices or accounts.
Integration With Metadata Analysis
Rate-limit data can be cross-checked with metadata such as OTP logs, submission timestamps, and geographic patterns. Together, these indicators strengthen the ability of officials to distinguish genuine requests from coordinated abuse.
By setting strict yet reasonable submission caps, detecting abnormal spikes, disrupting automation, and protecting both system stability and voters’ rights, rate-limiting significantly reduces the risk of bot-like misuse of Form-7 submissions online.
What Privacy-Safe Way Shares Form-7 Logs With Investigators
Sharing Form-7 logs with investigators is essential for detecting fraud, but it must be done without exposing sensitive voter information. A privacy-safe framework ensures accountability while protecting individual rights.
Use of Anonymized Metadata
Logs can be stripped of personally identifiable information such as voter names, EPIC numbers, and addresses. Instead, investigators should receive anonymized data points like IP addresses, submission timestamps, device IDs, OTP verification status, and geographic markers. These fields are sufficient to detect abnormal patterns without compromising voter identity.
Controlled Access Channels
Logs should be shared through secure, access-controlled portals rather than raw file transfers. Each investigator’s access must be logged, and data should be encrypted in transit and storage. This ensures accountability and prevents leaks.
Role-Based Data Sharing
Investigators do not require the same level of detail as Election Registration Officers. For example, EROs may need voter details to verify requests, but investigators analyzing fraud patterns only require aggregated and anonymized metadata. Restricting exposure based on role reduces privacy risks.
Masked Identifiers
Where necessary, voter identifiers can be replaced with hashed or tokenized versions. This allows investigators to track duplicate or repeated submissions without seeing the actual identity of the voter.
Time-Bound Access
Access to logs should be limited to specific time windows tied to active investigations. Expiring credentials and auto-deletion of shared datasets after use prevent long-term data exposure.
Audit Trails
Every instance of log sharing should generate an audit record, capturing who accessed the data, when, and for what purpose. These trails discourage misuse and strengthen the chain of custody for legal proceedings.
Integration of Aggregated Dashboards
Instead of providing raw logs, dashboards that visualize trends in Form-7 submissions, such as bursts by IP, duplicate attempts, or geographic anomalies, can be shared. This provides investigators with actionable insights while avoiding unnecessary exposure of individual-level records.
By relying on anonymization, controlled channels, role-based sharing, masked identifiers, time-limited access, and audit trails, election authorities can share Form-7 logs with investigators in a privacy-safe and accountable manner.
How to Train Booth-Level Officers to Flag Form-7 Irregularities
Booth-Level Officers (BLOs) serve as the first line of verification for electoral roll management, making their training crucial in identifying irregularities in Form-7 submissions. Effective training equips them to distinguish between genuine deletions and suspicious patterns that may indicate misuse.
Building Awareness of Form-7 Rules
Training should begin with clear instruction on the legal grounds for voter deletion through Form-7: death, migration, or disqualification. BLOs must understand the specific documents that support each reason and the procedures for notifying voters before any deletion is approved.
Familiarity With Common Red Flags
BLOs should be trained to identify red flags such as multiple requests citing the same reason without supporting evidence, clusters of deletion requests in the same booth, and identical handwriting or wording in offline forms. For digital submissions, awareness of bulk filings tied to specific localities or communities is critical.
Use of Technology Tools
Practical sessions should include hands-on training with mobile apps such as GARUDA and Voter Helpline App dashboards. BLOs must learn how to access request logs, review submission metadata, and cross-check deletion requests against voter rolls for their booth.
Verification Practices in the Field
BLOs should be trained to conduct quick field verification when multiple deletion requests target the same household or street. Techniques include door-to-door visits, confirmation from neighbors, and checking local records like death registers or migration certificates.
Escalation Protocols
Officers must know when to escalate cases to Election Registration Officers. Training should include scenarios where abnormal patterns, such as large-scale deletions from one community or suspiciously identical requests, require immediate reporting for further investigation.
Documentation and Reporting Discipline
BLOs should be instructed to maintain detailed records of their verification work, including notes from field visits, photographs of notices served, and signed acknowledgments from voters. These records provide accountability and protect against wrongful deletions.
Continuous Refresher Sessions
Since Form-7 misuse tactics may evolve, regular refresher workshops should be conducted. These can cover new anomaly detection methods, updated digital tools, and lessons learned from past cases of irregular deletions.
By combining legal knowledge, red-flag awareness, technology use, field verification skills, escalation protocols, and disciplined documentation, booth-level officers can be effectively trained to flag Form-7 irregularities and safeguard the integrity of electoral rolls.
Can Machine Learning Rank Suspicious Form-7 Applications Quickly
Machine learning can help election authorities process and prioritize large volumes of Form-7 applications by identifying suspicious ones faster than manual screening alone. By learning from past patterns of misuse and valid deletions, models can rank applications based on the likelihood of irregularity.
Feature Selection for Ranking
Key data points can be converted into model features. These include the frequency of submissions from a single IP, identical reasons cited across multiple applications, time-of-day patterns, repeated targeting of the same voter, and absence of supporting documents. By analyzing these features, the system can generate probability scores for each request.
Detection of Bulk and Scripted Activity
Unsupervised models such as clustering algorithms can group requests with highly similar attributes, exposing clusters that may have originated from centralized software or coordinated campaigns. For example, if hundreds of forms list the same wording for migration, the model can rank them higher for review.
Real-Time Prioritization
Machine learning systems can operate in real time, flagging high-risk applications as they arrive. Instead of reviewing all submissions sequentially, Election Registration Officers can first focus on those ranked as most suspicious, improving efficiency during intensive revision periods.
Integration With Verification Workflows
The ranking system can feed into ERO dashboards, displaying color-coded risk levels. Low-risk requests can follow standard processing, while medium- and high-risk applications are queued for additional checks, such as field verification or escalation to district authorities.
Continuous Model Training
Models must be updated with feedback from verified cases. If a flagged request is later confirmed fraudulent, the system learns from its attributes. Conversely, genuine deletions marked suspiciously help reduce false positives over time.
Safeguards for Fairness
To prevent bias, models should avoid over-reliance on demographic attributes and instead focus on behavioral and technical indicators. Transparency in how features contribute to ranking ensures that the process remains accountable.
By ranking Form-7 applications through anomaly detection, clustering, and risk scoring, machine learning can quickly highlight suspicious requests, allowing EROs to prioritize verification and reduce the chances of wrongful voter deletions.
What Citizen Checklist Confirms a Legitimate Form-7 Deletion
For voters, confirming whether a Form-7 deletion against their name is genuine requires following a clear checklist. This helps distinguish between valid administrative action and wrongful or fraudulent attempts to remove names from electoral rolls.
Official Notification Receipt
A legitimate deletion process begins with an official notice. Citizens should check whether they have received a written notice, SMS, or email from the Election Registration Officer (ERO) informing them about the Form-7 application filed against their entry. Lack of notification is an early warning sign of irregularity.
Verification of Grounds for Deletion
Form-7 allows deletion only in specific cases: death, migration, or disqualification. Citizens should verify whether the cited reason applies to them or a family member. If the reason does not match their situation, the request is likely invalid.
Availability of Supporting Documents
A valid Form-7 deletion must be backed by documentary evidence such as a death certificate, proof of new residence, or legal records of disqualification. Citizens can demand to see whether such evidence exists before accepting the deletion.
ERO and Booth-Level Officer Interaction
A Booth-Level Officer (BLO) may visit the household as part of verification. Citizens should confirm whether this visit occurred and whether they or their family provided input. Absence of BLO verification raises concerns about the legitimacy of the deletion.
Draft Roll Cross-Check
Citizens should check the draft electoral rolls published after Special Revision or routine updates. If their name appears marked for deletion without prior notice, it indicates a possible wrongful Form-7 application.
Right to File Objection
Every voter has the right to object to a proposed deletion within the notified period. A legitimate process ensures that the citizen is informed about this right and has a window of time to contest the request.
Tracking Through Official Platforms
Citizens can track Form-7 applications on the National Voter Service Portal (NVSP) or Voter Helpline App. A legitimate request will show as pending verification until officially approved, rather than disappearing abruptly from the rolls.
By confirming receipt of official notification, verifying the reason cited, checking supporting documents, ensuring BLO interaction, cross-checking draft rolls, exercising the right to object, and tracking applications online, citizens can reliably confirm whether a Form-7 deletion against their name is legitimate.
How Should ECI Publish Form-7 Transparency Reports Each Quarter
Quarterly transparency reports on Form-7 strengthen accountability in electoral roll management. By publishing structured and anonymized data, the Election Commission of India (ECI) can provide public visibility into how voter deletions are processed while safeguarding individual privacy.
Aggregated Statistics by Constituency
Reports should present the number of Form-7 applications received, approved, rejected, and pending in each constituency. Presenting data at this level provides clarity on regional patterns without disclosing voter-level details.
Categorization by Reason for Deletion
Applications should be grouped under death, migration, and disqualification categories. This breakdown allows observers to understand whether deletion trends reflect natural demographic changes or unusual spikes in specific categories.
Rejection and Objection Data
Reports should include figures on applications rejected for lack of proof, duplication, or malicious intent. Similarly, the number of objections raised by citizens against proposed deletions should be recorded. This demonstrates that due process was followed before removing names.
Anomaly and Bulk Filing Indicators
The report should highlight flagged cases where clusters exceeded thresholds, such as multiple applications from a single IP address or identical reasons used across dozens of forms. Tracking such anomalies ensures public confidence in fraud detection.
Timeframe Metrics
Each report should include average processing times for Form-7 applications. Publishing how long it takes to move from submission to final decision allows monitoring of efficiency while ensuring sufficient time is given for verification.
Citizen Safeguard Section
The report should summarize safeguards applied, such as notifications sent to voters, objection periods provided, and field verifications conducted by Booth-Level Officers. This section reinforces trust that names are not deleted without notice.
Open Data Format
Publishing the reports in machine-readable formats like CSV or JSON allows researchers, media, and political parties to analyze trends independently. Alongside this, a visual dashboard on the ECI website can display graphs and constituency-level comparisons for public use.
Independent Audit Summary
Each quarter’s report should include a brief audit statement confirming that flagged anomalies were reviewed by higher authorities or independent observers. This adds an external check to the Commission’s own reporting.
By combining constituency-wise statistics, categorized reasons, rejection data, anomaly tracking, processing timelines, citizen safeguards, open data formats, and audit summaries, the ECI can publish quarterly Form-7 transparency reports that build confidence in the integrity of electoral roll management.
What Does the Law Require Before Approving a Form-7 Deletion
The approval of a Form-7 request is not automatic. The Representation of the People Act, 1950 and the Registration of Electors Rules, 1960 lay down specific legal requirements that Election Registration Officers (EROs) must follow before a voter’s name can be removed from the rolls.
These requirements ensure that only ineligible names are deleted and that eligible citizens are not wrongfully disenfranchised.
Grounds Defined by Law
Form-7 can be filed only on three legal grounds: death of the voter, migration outside the constituency, or disqualification under the law (for example, due to loss of citizenship or legal restrictions). Any request outside these grounds cannot be approved.
Mandatory Verification by the ERO
The ERO is legally bound to verify every deletion request. Verification may include checking official death records, confirming migration through address proof, or validating disqualification orders. Without documentary or field-level confirmation, no deletion can proceed.
Notice to the Concerned Voter
Before approving a deletion, the law requires that the concerned voter be notified. Notices are served either through Booth Level Officers, post, SMS, or email. This gives the voter an opportunity to object if the request is false or malicious.
Objection Period
The voter or their family must be given a clear window of time to respond to the deletion notice. Only after this period expires without objection, or if objections are reviewed and dismissed with evidence, can the ERO proceed with approval.
Role of Booth Level Officers
BLOs play a critical role in compliance. They are tasked with visiting the residence of the voter to confirm whether the grounds cited are genuine. Their field verification report is an essential part of the approval process.
Documentation Requirements
The law requires supporting documents to be attached with the Form-7 application. For example, a death certificate, proof of residence outside the constituency, or court records in case of disqualification. EROs must record and retain this documentation before approving the deletion.
Right to Appeal
If a voter’s name is deleted despite objection, the law provides the right to appeal the decision to higher electoral authorities. This safeguard ensures accountability in the deletion process.
By enforcing strict grounds, requiring verification, mandating voter notification, providing an objection period, incorporating BLO reports, and retaining supporting documents, the law ensures that Form-7 deletions are lawful, transparent, and subject to checks before approval.
How to Restore Wrongly Deleted Voters After Faulty Form-7
When voters are wrongly deleted due to faulty or malicious Form-7 submissions, the election process must provide clear corrective mechanisms to restore their names. Ensuring swift restoration not only protects individual rights but also preserves the integrity of the electoral roll.
Filing a Fresh Form-6
The primary method for restoration is through Form-6, which allows a citizen to reapply for inclusion in the electoral roll. The applicant must submit proof of identity, age, and residence. Once verified by the Election Registration Officer (ERO), the name is restored in the voter list.
Objection and Appeal Route
If the deletion is discovered during the objection period after a draft roll is published, the voter can immediately file an objection with the ERO. Even after final rolls are published, voters have the right to appeal to the Chief Electoral Officer (CEO) or approach higher election authorities for redress.
Special Revision Window
During Special Summary or Intensive Revisions, voters whose names were wrongly deleted are given an opportunity to reapply. Election Commission guidelines usually instruct EROs to prioritize these cases, as wrongful deletions are considered administrative errors that need urgent correction.
Role of Booth Level Officers
Booth Level Officers (BLOs) assist in restoring wrongly deleted names by verifying residence and eligibility during field visits. Their reports act as key evidence for re-inclusion, particularly when voters lack full documentation but are locally recognized as residents.
Fast-Track Processing for Wrongful Deletions
ECI guidelines recommend that wrongful deletions flagged through complaints, public hearings, or political party objections should be placed on a fast-track verification cycle. These cases are reviewed quickly and added back to the rolls without waiting for the next routine update.
Technology-Based Reinstatement
Platforms such as the NVSP and Voter Helpline App allow citizens to check their status. If a wrongful deletion is detected, digital resubmission of Form-6 and grievance modules in these apps enable faster restoration, supported by online tracking for transparency.
Legal Safeguards
If wrongful deletions occur close to elections, affected voters may approach courts for relief. Courts have, in past cases, directed EROs to ensure that eligible voters are restored without delay, reinforcing the legal accountability of the election process.
By providing multiple restoration routes through Form-6, objection and appeal processes, special revision windows, BLO verification, fast-track mechanisms, and digital tools, the system ensures that voters wrongly deleted through faulty Form-7 submissions can regain their rightful place on the electoral roll.
Which Appeal Routes Exist if a Form-7 Deletes My Vote
When a voter’s name is deleted through Form-7, either wrongly or without proper verification, the law provides multiple appeal routes to ensure restoration of voting rights. These routes balance administrative remedies with legal recourse to protect citizens from disenfranchisement.
Immediate Approach to the Election Registration Officer (ERO)
The first appeal route is to approach the ERO of the constituency. A voter can file an objection or submit Form-6 for re-inclusion. Since the ERO is directly responsible for electoral roll management, this route is often the fastest for correction.
Escalation to the District Election Officer (DEO)
If the ERO does not address the complaint, the voter can escalate the matter to the District Election Officer. The DEO oversees ERO decisions and has the authority to review cases of wrongful deletions flagged by citizens, political parties, or civil groups.
Appeal to the Chief Electoral Officer (CEO) of the State
The state-level Chief Electoral Officer supervises the preparation and revision of electoral rolls. Citizens can submit a formal appeal or grievance to the CEO’s office if lower-level remedies fail. CEOs also publish public notices and can order expedited restoration during intensive revision exercises.
Election Commission of India (ECI) Complaint Mechanism
Citizens may file a complaint with the Election Commission of India through its online grievance portal or by petitioning directly. The ECI monitors large-scale irregularities, reviews misuse of Form-7, and can issue directions to state election authorities to restore names promptly.
Judicial Remedies
If administrative remedies do not resolve the matter, voters can approach the High Court under Article 226 of the Constitution or the Supreme Court under Article 32 for violation of their right to vote. Courts have previously directed election authorities to reinstate wrongly deleted voters, especially during election periods.
Political Party and Observer Intervention
During elections, political parties and election observers appointed by the ECI often raise complaints regarding wrongful deletions. Citizens can route grievances through these channels, which may prompt faster official review.
Digital and App-Based Appeals
Through the National Voter Service Portal (NVSP) and Voter Helpline App, voters can track their deletion status and lodge complaints online. These platforms route grievances to the appropriate officer for resolution while giving applicants a digital trail of their case.
By engaging with EROs, escalating to DEOs or CEOs, filing complaints with the ECI, using judicial remedies, or leveraging digital portals, citizens have multiple appeal routes if their vote is wrongly deleted via Form-7. This layered framework ensures both administrative efficiency and legal protection.
How Do EVM Ballot Changes Relate to Form-7 Roll Hygiene
Electronic Voting Machines (EVMs) operate based on the final, verified electoral roll. Any inaccuracies in the roll, including wrongful deletions through Form-7, directly affect who can cast a vote on polling day. The connection between EVM ballot changes and Form-7 roll hygiene lies in the synchronization of candidate lists, voter lists, and machine programming.
Dependency on Updated Electoral Rolls
Before an election, the final electoral roll is locked and provided to polling officials. If Form-7 deletions are mishandled, eligible voters may find their names missing from the roll, preventing them from being recognized at polling stations. This error flows into the EVM process since machines depend on accurate rolls to validate voter eligibility.
Alignment With Ballot Preparation
EVM ballots are programmed to display candidate names based on nominations, but the ability of voters to use these ballots depends on their presence in the rolls. Form-7 roll hygiene ensures that only legitimate deletions are approved, preventing disenfranchisement at the stage when EVMs are ready for deployment.
Avoidance of Mismatches on Polling Day
If voter lists contain wrongful deletions due to faulty Form-7 processing, the polling station staff may face disputes where eligible voters are denied access. This creates delays, disputes, and legal challenges. Clean rolls through careful Form-7 handling minimize such mismatches between EVM readiness and voter access.
Transparency in Audit Trails
When Form-7 deletions are properly verified and documented, they form part of the audit trail that can be cross-checked against EVM usage data. If disputes arise, authorities can demonstrate that only verified deletions were approved before ballot finalization.
Ensuring Public Trust in Machines
EVMs themselves are tamper-resistant, but the perception of fairness depends on the quality of the voter rolls feeding into them. Mishandled Form-7 deletions create suspicion that the rolls, rather than the machines, are manipulated.
Maintaining strict roll hygiene builds confidence that both the voter list and the EVM ballot reflect the same lawful process.
By ensuring that Form-7 deletions are verified, notified, and properly documented before final roll publication, the Election Commission prevents wrongful voter exclusion and ensures seamless integration between electoral rolls and EVM ballots.
This safeguards both operational efficiency and public trust in elections.
What Accessibility Measures Protect PwD Voters From Bad Form-7
Voters with disabilities (PwD) are more vulnerable to wrongful deletions through Form-7 because of barriers in communication, documentation, and verification. To protect their rights, the Election Commission of India (ECI) has introduced accessibility measures that ensure Form-7 misuse does not disenfranchise them.
Mandatory Notification in Accessible Formats
PwD voters must receive deletion notices in accessible formats such as large-print letters, Braille, SMS, and app-based alerts. This ensures they are informed if a Form-7 is filed against their name and can respond before removal.
Assistance Through Booth Level Officers (BLOs)
BLOs are required to give special attention to households with PwD voters. During field verification, BLOs must confirm the voter’s presence and eligibility directly or through family caregivers. This added step reduces the risk of wrongful deletions going unchallenged.
Dedicated PwD Helpdesks
Many constituencies now set up PwD helpdesks during revision periods. These desks handle complaints about wrongful deletions, guide PwD voters in filing objections, and ensure priority processing of re-inclusion requests when names are wrongly removed.
Integration With ERO-Net and NVSP
PwD voters can track their voter status through the NVSP portal or Voter Helpline App, which are designed with accessibility features like screen-reader compatibility. This allows them to check if a Form-7 deletion is pending against their name without needing physical visits.
Priority Restoration for Wrongful Deletions
If a PwD voter is wrongly deleted, election authorities treat their re-inclusion as a priority case. Fast-track restoration ensures they are not denied their right to vote in upcoming elections because of fraudulent or faulty Form-7 submissions.
Legal Safeguards
The Rights of Persons with Disabilities Act, 2016 mandates equal participation in the electoral process. Wrongful deletions of PwD voters can be contested under this law in addition to election-specific grievance routes, creating dual protection.
Community and NGO Support Channels
The ECI collaborates with disability rights groups and NGOs to monitor wrongful deletions affecting PwD voters. These organizations help file objections, raise awareness, and ensure grievances reach higher authorities when necessary.
By combining accessible notifications, BLO verification, PwD helpdesks, digital tracking tools, priority restoration, legal backing, and community support, the election system creates a protective framework that shields PwD voters from the effects of faulty or malicious Form-7 deletions.
How to Cross-Verify Form-7 With Address and Migration Data
Form-7 requests for deletion often cite migration or change of residence as the reason. To prevent wrongful removals, election officials must cross-verify these applications against reliable address and migration data.
Matching With Current Address Records
Officials check if the voter’s current address still falls within the same constituency. This involves verifying utility bills, Aadhaar-linked addresses, and ration card details. If the supporting documentation confirms residence, the Form-7 request is flagged as suspicious.
Field Verification by Booth Level Officers
Booth Level Officers (BLOs) visit the voter’s registered address to confirm whether the voter has shifted or continues to live there. Direct interaction with neighbors or household members provides additional confirmation of residence status.
Comparison With Form-6 Submissions
If a voter has recently filed a Form-6 to register at a new address, the Form-7 deletion request in their previous constituency becomes valid. Cross-verification of both forms ensures that deletions only occur when a new registration is confirmed elsewhere.
Use of Migration Databases
In areas with high labor migration, officials may consult state migration boards or local administrative records. This helps verify whether mass Form-7 requests are consistent with actual migration patterns rather than coordinated deletion attempts.
Cross-Checking With Electoral Roll Updates
During Special Summary Revision, applications for additions and deletions are processed together. Linking Form-7 requests with concurrent applications for inclusion in another constituency helps validate genuine cases and identify anomalies.
Technology-Based Matching
Election software such as ERO-Net can automatically flag cases where the same individual appears in both a deletion request (Form-7) and a new registration (Form-6). Geo-tagged field reports also assist in detecting false migration claims.
Handling Disputes
When address or migration data remains inconclusive, the Electoral Registration Officer (ERO) issues a notice to the voter. The deletion proceeds only after the voter fails to respond or provide proof of residence, safeguarding against wrongful removal.
Through systematic use of address documents, BLO field checks, migration records, technology-assisted matching, and notice-based verification, cross-checking ensures that Form-7 deletions are applied only to genuine migration cases and not exploited for voter suppression.
Can Identical Device Fingerprints Expose Mass Form-7 Attempts
Device fingerprinting is a forensic tool that election authorities can use to identify suspicious online behavior linked to Form-7 submissions. By analyzing technical markers, investigators can detect whether a large number of applications originate from the same or cloned devices.
What Device Fingerprints Capture
A device fingerprint records unique technical attributes of a device such as browser version, screen resolution, installed fonts, operating system, time zone, and IP metadata. Even if users mask IPs with VPNs, the combination of these parameters often creates a near-unique signature.
Detecting Mass Submissions
When multiple Form-7 requests share identical or near-identical fingerprints, it suggests automation or coordinated submissions from a single device or controlled cluster of devices. For instance, if hundreds of applications appear with the same browser build, OS version, and resolution within minutes, the system can flag them for review.
Cross-Referencing With Other Logs
Fingerprints gain more value when cross-verified with OTP logs, mobile numbers, and geo-location data. If the same device pattern links to different voter IDs across constituencies, it strengthens the evidence of manipulation.
Reducing False Positives
Not all identical fingerprints indicate fraud. Many voters in rural areas use public service kiosks, cyber cafés, or common mobile devices. To avoid penalizing genuine submissions, the Election Commission can combine fingerprint checks with field verification by Booth Level Officers.
Integration With Monitoring Tools
The NVSP, VHA, and GARUDA platforms can incorporate fingerprint monitoring into their backend systems. Automated alerts can highlight unusual clusters in real time, allowing Electoral Registration Officers (EROs) to suspend bulk requests until verification is complete.
Legal and Privacy Considerations
While device fingerprinting can reveal patterns of misuse, authorities must comply with data protection norms. Fingerprint data should remain accessible only to authorized officials, anonymized for reporting, and subject to clear retention limits.
Through controlled use of device fingerprints, combined with cross-verification, election authorities can quickly detect scripted or bot-driven Form-7 deletion campaigns while protecting genuine citizens who file requests through shared devices.
Penalties That Deter Malicious Bulk Form-7 Submissions
The misuse of Form-7 to delete genuine voters from the electoral roll is treated as an electoral offense in India. Several layers of penalties exist today to discourage bulk and malicious submissions.
Legal Provisions Under Electoral Law
The Representation of the People Act, 1950 and 1951 provides the foundation for penal action. Submitting false declarations, knowingly providing incorrect information, or attempting to remove legitimate voters can attract criminal charges. Sections dealing with false statements, impersonation, and obstruction of the electoral process apply directly to Form-7 misuse.
Criminal Liability
Individuals or groups engaging in fraudulent mass deletions may face imprisonment and fines. Depending on the scale of misconduct, penalties may extend to six months or more of imprisonment along with monetary fines. Repeat offenders or organized actors, especially when political influence is evident, may face harsher sentences under conspiracy or forgery charges.
Administrative Consequences
Electoral Registration Officers (EROs) can blacklist applicants, suspend suspicious submissions, and report offenders to law enforcement. Technology logs such as IP addresses, device fingerprints, and OTP verification records serve as evidence in such cases.
Political Accountability
If political parties or their workers are linked to coordinated Form-7 misuse, the Election Commission of India (ECI) can initiate inquiries, issue show-cause notices, and in severe cases, recommend de-recognition of a party or cancel its symbol usage. This political cost serves as an additional deterrent.
Cybercrime and IT Act Enforcement
Large-scale manipulation through automated bots, fake devices, or misuse of centralized software may also invoke provisions of the Information Technology Act, 2000. Unauthorized access to election platforms or scripting bulk submissions can be prosecuted as cybercrime.
Enforcement Challenges
Although penalties exist, enforcement depends on strong evidence gathering. Delays in prosecution or lack of follow-through can weaken deterrence. Strengthening monitoring systems, mandating quarterly transparency reports, and ensuring rapid FIR registration against offenders can increase the credibility of penalties.
Deterrent Effect
The combination of criminal prosecution, political consequences, and cybercrime enforcement is designed to discourage malicious Form-7 misuse. However, its effectiveness relies on strict and timely application by the ECI, district election officers, and police authorities.
Reporting Form-7 Claims Versus Verified Facts
The handling of media coverage around Form-7 is sensitive because claims of voter deletion can influence trust in elections. Responsible reporting requires a separation of allegations from confirmed information.
Clear Distinction Between Claims and Verification
Media should explicitly label whether a piece of information is an allegation, a pending investigation, or a confirmed fact. Claims by political parties or individuals should be presented as assertions, not as established truths. Verified data from the Election Commission of India (ECI) or Electoral Registration Officers (EROs) should be cited separately with documentary support.
Reliance on Primary Sources
Reporters should avoid depending solely on party statements or social media narratives. Instead, they must cross-check with official records such as ECI press releases, district election office data, or transparency dashboards. This reduces the risk of amplifying misinformation.
Contextual Explanation
When presenting claims, media should also explain the legal and procedural framework of Form-7, such as the requirement for notices, verification steps, and the right to appeal. This ensures that the audience understands the difference between procedural delays and actual malpractice.
Use of Neutral Language
Loaded terms such as “mass deletion conspiracy” or “fraudulent wipeout” should be avoided until evidence is established. Instead, reports should use neutral descriptions like “alleged irregularities,” “pending verification,” or “flagged applications.”
Fact-Checking Protocols
Media outlets should adopt structured fact-checking workflows. For instance, when a political party claims 5,000 voters were deleted, the report should state whether this number was cross-verified against ECI or district-level data. If not, the report should clearly mark the figure as unverified.
Balanced Coverage
Coverage must ensure that both the complainant’s voice and the ECI’s response are included in the same report. Publishing only allegations without presenting the official version risks creating partial or misleading narratives.
Protection Against Panic
Headlines should not exaggerate claims of voter deletion without supporting evidence. Sensational framing can erode public confidence in elections. A measured tone with clear attribution to sources helps maintain trust while still highlighting issues.
Transparency About Uncertainty
If facts are still under review, media should communicate this openly. Phrases like “under verification by the district election office” or “awaiting ECI response” provide clarity while preventing premature conclusions.
Key Performance Indicators for District-Level Form-7 Scrutiny
The efficiency and fairness of Form-7 scrutiny can be evaluated through defined Key Performance Indicators (KPIs). These indicators help the Election Commission of India (ECI) and observers assess whether districts are handling deletions with accuracy, speed, and transparency.
Processing Timeliness
One KPI is the average time taken to review and decide on a Form-7 application. Districts that consistently delay scrutiny risk undermining public trust and allowing backlogs to accumulate. Monitoring turnaround time ensures that applications are neither rushed without checks nor kept pending unnecessarily.
Verification Accuracy
The accuracy of verification can be measured by comparing Form-7 decisions with subsequent appeals or corrections. A high rate of wrongful deletions later restored through appeals indicates weak scrutiny. Districts with low reversal rates demonstrate stronger verification practices.
Rejection-to-Approval Ratio
The ratio of rejected to approved Form-7 requests helps flag whether scrutiny is too lenient or overly restrictive. Sudden spikes in approvals or rejections without supporting documentation suggest the need for closer supervision.
Duplicate Detection Rate
Another KPI is the ability to identify and block duplicate or scripted submissions. Districts should record the percentage of detected duplicates within total submissions. High detection rates indicate strong vigilance, while low detection rates may reveal overlooked fraud attempts.
Field Inquiry Compliance
ERO guidelines often require physical verification or booth-level officer (BLO) inquiry for suspicious applications. A KPI can track the proportion of Form-7 cases where field verification was completed within the mandated timeline.
Appeal and Complaint Resolution
Monitoring how quickly and fairly districts resolve complaints about wrongful deletions provides insight into accountability. The number of unresolved appeals or escalations to state-level Chief Electoral Officers (CEOs) serves as a measure of responsiveness.
Transparency Metrics
Publishing periodic district-level reports on Form-7 scrutiny, including counts of submissions, rejections, and pending cases, is a transparency KPI. Districts that proactively share data help build public confidence and discourage misuse.
Fraud Pattern Detection
Districts should also be assessed on their ability to detect anomaly clusters such as identical reasons, same device fingerprints, or bulk requests from one IP address. Tracking how many of these clusters are flagged per quarter measures effectiveness in fraud detection.
Civil Society’s Role in Monitoring Form-7 Trends Responsibly
Civil society organizations (CSOs), election watchdogs, and advocacy groups can play a constructive role in ensuring transparency and accountability around Form-7 deletions. Responsible monitoring requires a balance between vigilance and avoiding the spread of misinformation.
Accessing Public Data
Civil society can track official electoral roll updates published by the Election Commission of India (ECI). By comparing quarterly reports, district-level summaries, and transparency dashboards, they can identify patterns in Form-7 deletions without relying on unverified claims. This ensures that monitoring is grounded in verified data sources.
Identifying Statistical Patterns
CSOs can use aggregated datasets to analyze unusual spikes in Form-7 submissions. For example, sudden increases in deletions in a specific constituency, or large-scale rejections clustered under the same reason, may signal anomalies. Data-driven analysis helps highlight areas requiring official inquiry without making premature allegations.
Collaborating with Election Officials
Civil society groups can engage constructively with Electoral Registration Officers (EROs) by submitting analytical reports on suspicious trends. Instead of publicizing unverified findings, these reports should be formally shared with election authorities for investigation. This channel reduces the risk of politicizing raw data.
Training Citizen Observers
Civil society can train citizen volunteers to monitor local electoral roll updates responsibly. Training should cover how to distinguish legitimate migration-based deletions from questionable bulk removals. Volunteers should also be guided on documenting findings in structured formats to avoid anecdotal or biased reporting.
Promoting Public Awareness
CSOs can run awareness campaigns explaining voter rights, Form-7 misuse risks, and available appeal mechanisms. Educating citizens ensures they check their voter status during revision periods and act quickly if their names are wrongly deleted. Awareness campaigns must be factual and avoid speculative claims.
Safeguarding Privacy
Monitoring must respect individual privacy. Civil society groups should never publish personal details of voters flagged in deletion lists. Instead, analysis should focus on aggregate data such as trends by constituency, district, or reason codes. Protecting privacy while highlighting systemic issues ensures ethical monitoring.
Coordinating with Other Stakeholders
Responsible monitoring also means collaboration with media, academia, and election observers. By cross-verifying findings with multiple stakeholders, civil society reduces the risk of misinterpretation and strengthens accountability efforts.
Identical Phone Numbers as Indicators in Form-7
Phone numbers serve as a key authentication factor in the online filing of Form-7. When the same number appears across multiple applications, it often signals irregular usage patterns. While duplication does not automatically prove fraud, it provides a strong indicator that calls for deeper scrutiny.
Assessing Legitimate Explanations
In some cases, repeated phone numbers may reflect legitimate circumstances. For instance, a single family member may use their phone to file Form-7 on behalf of multiple relatives, particularly in rural areas where not every voter owns a mobile number. Similarly, shared community numbers may be linked to multiple electors in low-connectivity regions. These scenarios require local verification rather than automatic rejection.
Identifying Suspicious Clusters
When the same phone number appears across dozens or hundreds of Form-7 applications spanning multiple households or constituencies, it raises suspicion of bulk submissions. Such clusters often indicate coordinated campaigns, misuse of digital credentials, or attempts to mass-delete electors. Electoral officers should flag these cases for verification and seek clarification from applicants.
Cross-Matching with Metadata
Phone numbers should be analyzed alongside other metadata such as IP addresses, device fingerprints, and timestamps. If identical numbers also coincide with the same network origin or submission timeframes, the likelihood of manipulation increases. These combined signals provide a stronger evidentiary base for escalation.
Verification and Accountability
To confirm legitimacy, Electoral Registration Officers (EROs) can initiate targeted phone verification, requesting confirmation from the linked voter. If calls or OTP validation reveal that the number holder was unaware of the deletions, it becomes clear evidence of unauthorized use. Documentation of such verification ensures accountability and prevents wrongful deletions.
Balancing Privacy and Oversight
Phone numbers are sensitive personal data, so investigations must protect privacy while enabling scrutiny. Analysis should remain at an aggregated level in public reporting, with direct identifiers disclosed only to election authorities during audits. This approach safeguards both voter rights and transparency.
Building a 24-Hour Form-7 Anomaly Response Playbook
A rapid-response playbook ensures that suspicious Form-7 activities are identified, verified, and acted upon without delay. The framework must combine automated detection, human verification, and structured escalation so that false deletions do not compromise voter rights.
Initial Detection and Alerting
Anomaly detection systems should run in near real-time to flag irregular submission patterns. These may include sudden spikes in applications from a single IP, clusters with identical phone numbers, or unusual time-of-day activity. Once flagged, alerts must be routed instantly to both the Electoral Registration Officer (ERO) and a district-level control room.
Categorization of Anomalies
Not all anomalies demand the same response. A triage layer should classify alerts into low, medium, or high severity. Low-severity anomalies, such as a family using one device, can be logged for review. High-severity anomalies, such as hundreds of deletion requests linked to the same device fingerprint, require immediate intervention.
Verification and Containment
Within the first six hours, field verification teams or automated OTP callbacks should be deployed to validate a sample of suspicious applications. If irregularities are confirmed, authorities should temporarily suspend processing of the flagged batch. This prevents wrongful deletions while further investigation continues.
Coordination Between Stakeholders
The playbook should define clear communication lines between EROs, district election officers, police cyber cells, and technical support units. Each actor must know their role: EROs for scrutiny, technical teams for data analysis, and law enforcement for potential misuse cases. Shared dashboards can reduce delays in coordination.
Escalation Protocols
If verified anomalies indicate systematic attempts at manipulation, the matter should escalate to the Chief Electoral Officer within 12 hours. Escalation triggers include mass attempts across multiple constituencies, evidence of automated submissions, or cross-district coordination. Higher authorities can then decide on legal proceedings and corrective measures.
Public Assurance Measures
By the 24-hour mark, provisional reports should be generated summarizing anomalies, verification status, and steps taken. These reports should be shared internally with election officers and, where appropriate, communicated publicly in aggregate form. This strengthens voter trust and discourages misinformation about deletions.
Continuous Improvement
Every 24-hour response cycle should conclude with a review to refine detection rules, improve triage thresholds, and update training for booth-level officers. This adaptive process ensures the playbook remains effective as new manipulation techniques emerge.
Quickest Citizen Method to Check Roll Deletions
Citizens can verify if their names have been removed from the electoral roll by using official online and offline mechanisms. These checks help individuals quickly confirm their voter status after suspected misuse of Form-7.
Online Roll Search
The National Voter Service Portal (NVSP) and the Voter Helpline App (VHA) provide direct access to updated electoral rolls. By entering details such as name, EPIC number, or registered address, citizens can confirm whether their record is still active. This method offers near-instant verification once the rolls are updated.
District CEO Websites
Every state and district CEO office publishes the latest electoral rolls online. Citizens can download the updated PDF rolls for their polling station or ward and cross-check their entries. This method allows bulk verification for families or neighborhoods and is especially useful when local reports suggest large-scale deletions.
SMS and Helpline Services
In several states, SMS-based lookup and toll-free helplines are available. By sending the EPIC number to a designated short code or calling the official helpline, voters can confirm their registration status without internet access.
Booth-Level Verification
Citizens may visit their Booth Level Officer (BLO) or designated voter facilitation center to check physical copies of rolls. BLOs maintain updated rolls and can confirm whether a deletion has been processed against a voter’s entry. This option also allows immediate filing of claims if wrongful deletion is detected.
Social Verification in High-Risk Areas
In constituencies with large-scale Form-7 filings, citizen groups or civil society organizations often assist with neighborhood-level roll verification. While unofficial, these checks alert voters to review their records promptly through official platforms.
Integrated Best Practice
For speed and reliability, the quickest method combines an online check via NVSP or VHA with physical verification at the BLO office. This ensures that errors detected digitally are confirmed on the ground, allowing citizens to act immediately if wrongful deletion is found.
Building Constituency Heatmaps of Form-7 Activity Safely
Tracking and visualizing Form-7 submissions across constituencies can reveal irregularities, but the process must protect voter privacy and follow legal safeguards. Heatmaps provide Election Officers and oversight bodies with a clear visual tool to monitor suspicious activity while avoiding exposure of personal details.
Data Aggregation
The process begins with aggregating Form-7 activity at the polling station, ward, or constituency level rather than exposing individual voter records. Only metadata such as submission volume, time of filing, frequency from identical devices, and common reasons cited for deletion should be used. This ensures that personally identifiable information is excluded.
Anonymization Protocols
Before mapping, all voter-level identifiers must be stripped. EPIC numbers, phone details, or IP addresses should never be displayed directly. Instead, anonymized IDs or hashed identifiers can be used for internal monitoring. For public-facing dashboards, only aggregated totals and comparative metrics should be presented.
Visualization Rules
Heatmaps should highlight intensity zones of Form-7 filings over specific time intervals, for example, daily or weekly clusters. District and constituency boundaries can serve as the base layer, with color gradients representing filing density. Sudden spikes in specific booths or clusters will immediately stand out, enabling targeted audits.
Threshold Alerts
The system should integrate thresholds that trigger alerts when filings exceed expected norms. For example, a surge of deletions in a single booth exceeding 5 percent of registered voters within 24 hours can automatically flag the area for review by the Electoral Registration Officer (ERO).
Controlled Access
Access to raw datasets must be restricted to EROs, District Election Officers, and authorized auditors. If heatmaps are published publicly, only safe summaries such as percentage changes or comparative trends across constituencies should be displayed. This prevents misuse of sensitive voter data while still maintaining transparency.
Review Workflow
Once anomalies are detected, flagged constituencies should undergo layered verification. BLOs can confirm whether the flagged deletions are genuine, while District Election Officers can cross-check with migration and death records. Media reporting on such heatmaps should rely only on officially validated trends to prevent misinformation.
Safe Implementation
A secure implementation combines data aggregation, anonymization, and tiered access. Internally, detailed heatmaps allow real-time monitoring and fraud detection, while externally, simplified maps reassure the public that roll hygiene is being actively maintained without revealing voter-specific information.
Audit Trails NVSP Must Retain for Form-7 Scrutiny
The National Voters’ Service Portal (NVSP) plays a central role in managing digital submissions of Form-7, which are requests to delete voter entries from the rolls. To ensure transparency and accountability, NVSP must retain a complete audit trail that enables Election Registration Officers (EROs) and investigators to trace every action linked to a Form-7 application. These trails safeguard against misuse and allow rapid verification of both genuine and fraudulent requests.
Submission Metadata
Every Form-7 entry should carry metadata including submission timestamp, originating IP address, device fingerprint, and session ID. This information helps identify bulk or scripted attempts by highlighting unusual submission patterns such as multiple deletions within seconds from the same device.
Authentication Records
NVSP must preserve the full log of authentication steps used during the filing, including OTP validation attempts, phone number linked, and whether the OTP was entered successfully. Retaining both successful and failed attempts ensures detection of brute force or repeated OTP misuse.
User Identity Logs
The system should capture identifiers such as the applicant’s EPIC number, linked mobile number, and associated address at the time of filing. This enables cross-verification of whether the request genuinely originates from the concerned voter or represents an external attempt to delete them.
Application Journey
The portal should log the sequence of actions taken by the filer, such as form fields filled, reasons for deletion selected, and any attachments uploaded. Retaining the order of actions helps auditors detect automated bots that fill forms in identical sequences.
System-Level Checks
Error messages, validation failures, and rejected submissions should also be logged. These entries help establish whether the system itself prevented irregular attempts and provide a baseline for measuring the effectiveness of inbuilt safeguards.
Approval and Review Logs
Once a Form-7 is filed, NVSP must maintain a chain of custody log. This should include the ERO who reviewed the request, any BLO verification visit logged in GARUDA or VHA apps, and the final approval or rejection decision with timestamp. The system must link the official’s digital signature or login credentials to every action.
Data Integrity Measures
Audit trails must be tamper-proof and stored securely in compliance with data protection rules. NVSP should apply hash-based integrity checks and maintain backups to ensure no log entries are altered or erased. Restricted access controls are necessary so only authorized officials can view or extract logs.
Transparency Layer
While raw audit trails remain internal, NVSP can share anonymized summaries such as rejection percentages, duplicate filing counts, and OTP misuse attempts in quarterly transparency reports. This balances privacy with public accountability.
Preventing Third-Party Apps from Abusing Form-7 Submission APIs
Form-7 submissions through the National Voters’ Service Portal (NVSP), VHA, and GARUDA apps are designed to be secure, but the presence of exposed or misused APIs can allow unauthorized third-party applications to automate large-scale deletion requests.
Protecting these APIs is critical to safeguarding the electoral roll.
Strong Authentication Controls
APIs must enforce strict authentication mechanisms tied to official portals and applications only. API keys or tokens should be issued exclusively to Election Commission systems, with no public endpoints for third-party access.
Tokens must also expire quickly and use multi-factor verification before permitting any write operation such as Form-7 submission.
Request Origin Verification
Each request should be validated for its origin. Whitelisting official domains, validating referrer headers, and embedding cryptographic signatures in requests can block third-party applications from masquerading as genuine clients.
In addition, enforcing TLS with certificate pinning ensures data is exchanged only between trusted endpoints.
Rate Limiting and Throttling
To prevent bulk abuse, the API should apply request throttling at multiple levels. This includes per-user, per-device, and per-IP rate limits.
Sudden spikes in submissions, such as hundreds of deletion requests within a short window, should trigger automated holds for manual verification by Election Registration Officers (EROs).
Session Binding and OTP Enforcement
Every API call for Form-7 must be tied to a verified voter session. OTP validation through registered mobile numbers must remain mandatory, and logs of both successful and failed attempts should be retained.
Without an OTP session, the system should reject API requests outright, blocking third-party tools from automating deletions.
Payload Integrity Checks
The system should validate payloads for anomalies such as identical reasons, duplicate EPIC numbers, or repeated addresses across multiple requests.
Hash-based request signing and checksum validation can ensure that only genuine, unaltered submissions from approved applications are accepted.
Monitoring and Anomaly Detection
Continuous monitoring should flag suspicious patterns such as identical device fingerprints, uniform user-agents, or repeated submission templates.
These anomalies often signal scripted automation by external tools. Automated alerts can direct EROs or cybersecurity cells to investigate.
Restricted API Documentation and Access
API specifications related to voter roll operations should remain internal. Public-facing documentation should exclude deletion endpoints, preventing malicious developers from replicating or reverse-engineering workflows.
Internal staff should access documentation under strict audit trails.
Legal and Disciplinary Measures
To reinforce technical controls, the Election Commission must explicitly define penalties for unauthorized use of Form-7 APIs under electoral law and the IT Act. Public communication that misuse can trigger prosecution discourages actors from experimenting with third-party automation.
Conclusion: Voter ID Form-7 and Misuse Safeguards
Form-7 plays a critical role in maintaining the integrity of India’s electoral rolls by allowing citizens to request the removal of names due to death, migration, or duplication.
However, its online availability through NVSP, VHA, and GARUDA makes it vulnerable to misuse through bulk, automated, or fraudulent deletions.
The Election Commission of India (ECI) has established safeguards that prevent any direct deletion from happening automatically.
Every request undergoes verification by the Electoral Registration Officer (ERO), supported by field inquiries, OTP validation, and supporting documents. To strengthen the process, technical measures such as rate-limiting, device fingerprinting, API origin verification, and anomaly detection are essential.
Operational safeguards, including quick triage rules, district-level KPIs, transparency reports, and Special Intensive Revisions, ensure accountability and timely corrections.
Civil society and media also play a role by monitoring Form-7 trends responsibly, distinguishing between unverified claims and verified facts.
Legal provisions under the Representation of the People Act and IT Act provide penalties against malicious or bulk misuse, while appeal routes and restoration processes protect voters who are wrongly deleted.
The combined approach of technical controls, administrative verification, public monitoring, and legal deterrence ensures that Form-7 remains a legitimate tool for electoral hygiene rather than a vulnerability for manipulation.
The focus moving forward should be on real-time detection, transparent reporting, and citizen-friendly mechanisms to quickly restore legitimate voters if errors occur.
Voter ID Form-7 Do in India: FAQs
What Is Form-7 Used for in India?
Form-7 allows citizens to request deletion of names from the electoral roll due to death, migration, duplication, or ineligibility.
How Does Form-7 Differ from Form-6 and Form-8?
Form-6 is for adding new voters, Form-8 is for corrections or updates, and Form-7 is for deletions.
Can Citizens Delete Votes Online Through Form-7?
Yes, citizens can submit Form-7 online, but no deletion happens automatically. EROs verify every request before approving.
What Are “Unsuccessful Attempts” in Form-7 Submissions?
These are rejected requests where the ERO finds insufficient evidence, duplicate entries, or mismatched records.
How Can Misuse of Form-7 Deletions Be Detected Quickly?
Cross-checking IP addresses, phone numbers, OTP logs, and document authenticity helps spot misuse within hours.
What Red Flags Suggest Coordinated Form-7 Deletions?
Patterns such as bulk filings from the same IP, identical reasons, or repeated phone numbers raise alarms.
How Should EROs Verify Bulk Online Form-7 Applications?
EROs should run automated duplicate checks, compare entries with migration and death records, and flag anomalies for manual review.
What Quick Checks Identify Duplicate Form-7 Requests?
Comparisons of voter ID numbers, linked phone numbers, and device fingerprints reveal duplicates.
How to Detect Deletion Bursts from Single IP Addresses?
Tracking submission frequency per IP and applying rate-limits helps detect bot-driven deletion attempts.
Which Metadata Is Most Useful in Detecting Form-7 Misuse?
IP logs, device fingerprints, OTP usage data, timestamps, and geo-location patterns are critical indicators.
How Do NVSP, VHA, and GARUDA Apps Process Form-7 Flows?
They act as front-end platforms to capture Form-7 requests, authenticate via OTP, and pass them to EROs for scrutiny.
What Is the Fastest Workflow for Auditing Form-7 Requests?
Batch grouping by geography, automated duplicate filtering, and targeted field verification ensure faster audits.
Can OTP and Phone Logs Reveal Manipulation?
Yes, repeated OTP requests on the same number or clustered phone usage for many deletions can expose misuse.
What Did the ECI Say About Online Deletions via Form-7?
The ECI clarified that deletions are not automatic, as every request undergoes verification before approval.
How Many Form-7 Applications Were Flagged in the Aland Case?
Thousands of suspicious deletion requests were flagged, exposing large-scale misuse attempts.
What Penalties Exist for Malicious Form-7 Misuse?
Penalties include imprisonment up to one year or fines under the Representation of the People Act and IT Act.
What Safeguards Prevent Centralized Software Abuse of Form-7?
API authentication, rate-limits, digital signatures, and audit trails reduce centralized manipulation risks.
How Can Wrongly Deleted Voters Be Restored?
Citizens can reapply through Form-6, approach EROs, or file appeals with the District Election Officer.
What Appeal Routes Exist if a Vote Is Deleted?
Appeals can be filed with EROs, Chief Electoral Officers, or moved to higher legal forums such as courts.
How Can Civil Society Monitor Form-7 Responsibly?
By analyzing published data, respecting privacy, engaging with EROs, and avoiding unverified allegations.











